Page 28 - DCAP309_INFORMATION_SECURITY_AND_PRIVACY
P. 28
Information Security and Privacy
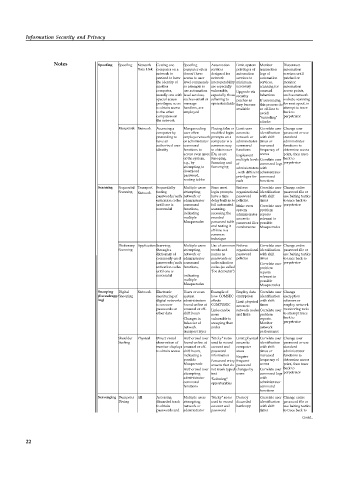
Notes Spoofing Spoofing Network Getting one Spoofing Automation Limit system Monitor Disconnect
Data Link computer on a computer often services privileges of transaction automation
network to doesn’t have designed for automation logs of services until
pretend to have access to user network services to automation patched or
the identity of level commands interoperability minimum services, monitor
another so attempts to are especially necessary scanning for automation
computer, use automation vulnerable, Upgrade via unusual access points,
usually one with level services, especially those security behaviors such as network
special access such as email or adhering to patches as If automating sockets, scanning
privileges, so as message open standards they become this process do for next spoof, in
to obtain access handlers, are available so off-line to attempt to trace
to the other employed avoid back to
computers on "tunneling" perpetrator
the network attacks
Masquerade Network Accessing a Masquerading Placing false or Limit user Correlate user Change user
computer by user often modified login access to identification password or use
pretending to employs network prompts on a network or with shift standard
have an or administrator computer is a administrator times or administrator
authorized user command common way command increased functions to
identity functions to to obtain user functions frequency of determine access
access even more IDs, as are Implement access point, then trace
of the system, Snooping, multiple levels Correlate user back to
e.g., by Scanning and of command logs perpetrator
attempting to Scavenging
administrators with
download , with different administrator
password, privileges for command
routing tables each functions
Scanning Sequential Transport Sequentially Multiple users Since most Enforce Correlate user Change entire
Scanning Network testing attempting login prompts organizational identification password file or
passwords/auth network or have a time password with shift use baiting tactics
entication codes administrator delay built in to policies. times to trace back to
until one is command foil automated Make even Correlate user perpetrator
successful functions, scanning, system problem
indicating accessing the administrator reports
multiple encoded access to relevant to
Masquerades password table password files possible
and testing it cumbersome Masquerades
off-line is a
common
technique
Dictionary Application Scanning Multiple users Use of common Enforce Correlate user Change entire
Scanning through a attempting words and organizational identification password file or
dictionary of network or names as password with shift use baiting tactics
commonly used administrator passwords or policies times to trace back to
passwords/auth command authentication Correlate user perpetrator
entication codes functions, codes (so called problem
until one is "Joe Accounts") reports
successful indicating relevant to
multiple possible
Masquerades Masquerades
Snooping Digital Network Electronic Users or even Example of Employ data Correlate user Change
(Eavesdropp Snooping monitoring of system how COMSEC encryption identification encryption
ing) digital networks administrators affects Limit physical with shift schemes or
to uncover found online at COMPUSEC access to times employ network
passwords or unusual or off- Links can be network nodes Correlate user monitoring tools
other data shift hours more and links problem to attempt trace
Changes in vulnerable to reports. back to
behavior of snooping than Monitor perpetrator
network nodes network
transport layer performance
Shoulder Physical Direct visual Authorized user "Sticky" notes Limit physical Correlate user Change user
Surfing observation of found online at used to record access to identification password or use
monitor displays unusual or off- account and computer with shift standard
to obtain access shift hours, password areas times or administrator
indicating a information Require increased functions to
possible Password entry frequent frequency of determine access
Masquerade screens that do password access point, then trace
Authorized user not mask typed changes by Correlate user back to
attempting text users command logs perpetrator
administrator "Loitering" with
command opportunities administrator
functions command
functions
Scavenging Dumpster All Accessing Multiple users "Sticky" notes Destroy Correlate user Change entire
Diving discarded trash attempting used to record discarded identification password file or
to obtain network or account and hardcopy with shift use baiting tactics
passwords and administrator password times to trace back to
other data command information Correlate user perpetrator
functions, System problem Contd...
indicating administrator reports
multiple printouts of relevant to
22 LOVELY PROFESSIONAL UNIVERSITY