Page 244 - DCAP104_EXPOSURE_TO_COMPUTER_DISCPLINES
P. 244
Unit 13: Understanding the Need of Security Measures
The object of security is to protect valuable or sensitive organizational information while making Notes
it readily available. Attackers trying to harm a system or disrupt normal business operations
exploit vulnerabilities by using various techniques, methods, and tools. System administrators
need to understand the various aspects of security to develop measures and policies to protect
assets and limit their vulnerabilities.
Attackers generally have motives or goals for example, to disrupt normal business operations
or steal information. To achieve these motives or goals, they use various methods, tools, and
techniques to exploit vulnerabilities in a computer system or security policy and controls.
13.1.5 Security Threats
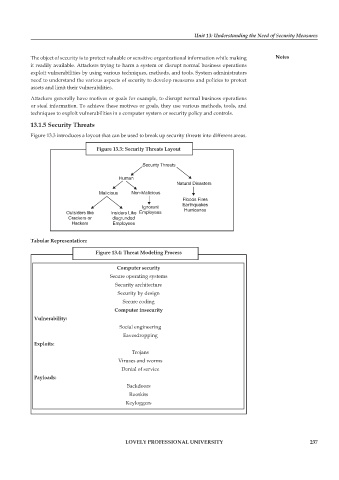
Figure 13.3 introduces a layout that can be used to break up security threats into different areas.
Figure 13.3: Security Threats Layout
Tabular Representation:
Figure 13.4: Threat Modeling Process
Computer security
Secure operating systems
Security architecture
Security by design
Secure coding
Computer insecurity
Vulnerability:
Social engineering
Eavesdropping
Exploits:
Trojans
Viruses and worms
Denial of service
Payloads:
Backdoors
Rootkits
Keyloggers
LOVELY PROFESSIONAL UNIVERSITY 237