Page 160 - DCAP516_COMPUTER_SECURITY
P. 160
Computer Security
Notes The level of security you establish will determine how many of these threats can be stopped by
your firewall. The highest level of security would be to simply block everything. Obviously
that defeats the purpose of having an Internet connection. But a common rule of thumb is to
block everything, then begin to select what types of traffic you will allow.
You can also restrict traffic that travels through the firewall so that only certain types of
information, such as e-mail, can get through. This is a good rule for businesses that have an
experienced network administrator that understands what the needs are and knows exactly
what traffic to allow through.
For most of us, it is probably better to work with the defaults provided by the firewall developer
unless there is a specific reason to change it. One of the best things about a firewall from a
security standpoint is that it stops anyone on the outside from logging onto a computer in your
private network.
While this is a big deal for businesses, most home networks will probably not be threatened in
this manner. Still, putting a firewall in place provides some peace of mind.
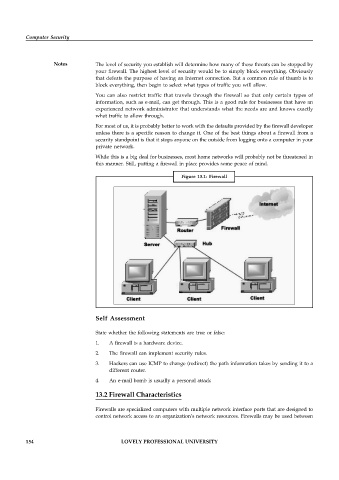
Figure 13.1: Firewall
Self Assessment
State whether the following statements are true or false:
1. A firewall is a hardware device.
2. The firewall can implement security rules.
3. Hackers can use ICMP to change (redirect) the path information takes by sending it to a
different router.
4. An e-mail bomb is usually a personal attack
13.2 Firewall Characteristics
Firewalls are specialized computers with multiple network interface ports that are designed to
control network access to an organization’s network resources. Firewalls may be used between
154 LOVELY PROFESSIONAL UNIVERSITY