Page 166 - DCAP516_COMPUTER_SECURITY
P. 166
Computer Security
Notes
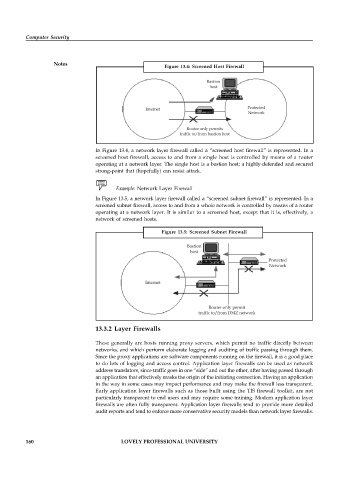
Figure 13.4: Screened Host Firewall
In Figure 13.4, a network layer firewall called a “screened host firewall” is represented. In a
screened host firewall, access to and from a single host is controlled by means of a router
operating at a network layer. The single host is a bastion host; a highly-defended and secured
strong-point that (hopefully) can resist attack.
Example: Network Layer Firewall
In Figure 13.5, a network layer firewall called a “screened subnet firewall’’ is represented. In a
screened subnet firewall, access to and from a whole network is controlled by means of a router
operating at a network layer. It is similar to a screened host, except that it is, effectively, a
network of screened hosts.
Figure 13.5: Screened Subnet Firewall
13.3.2 Layer Firewalls
These generally are hosts running proxy servers, which permit no traffic directly between
networks, and which perform elaborate logging and auditing of traffic passing through them.
Since the proxy applications are software components running on the firewall, it is a good place
to do lots of logging and access control. Application layer firewalls can be used as network
address translators, since traffic goes in one “side” and out the other, after having passed through
an application that effectively masks the origin of the initiating connection. Having an application
in the way in some cases may impact performance and may make the firewall less transparent.
Early application layer firewalls such as those built using the TIS firewall toolkit, are not
particularly transparent to end users and may require some training. Modern application layer
firewalls are often fully transparent. Application layer firewalls tend to provide more detailed
audit reports and tend to enforce more conservative security models than network layer firewalls.
160 LOVELY PROFESSIONAL UNIVERSITY