Page 179 - DCAP516_COMPUTER_SECURITY
P. 179
Unit 14: Intrusion Detection System and Secure E-mail
specifications on network traffic. Also, some application layer firewalls have also integrated Notes
IPS-style signatures into their products to provide real-time analysis and blocking of traffic.
Application firewalls do have IP addresses on their ports and are directly addressable. Moreover,
they use full proxy features to decode and reassemble packets. Not all IPS perform full proxy-
like processing. Also, application-layer firewalls tend to focus on firewall capabilities, with IPS
capabilities as add-on. While there are numerous similarities between the two technologies,
they are not identical and are not interchangeable.
Unified Threat Management (UTM), or sometimes called “Next Generation Firewalls” are also
a different breed of products entirely. UTM products bring together multiple security capabilities
on to a single platform.
A typical UTM platform will provide firewall, VPN, anti-virus, web filtering, intrusion prevention
and anti-spam capabilities. Some UTM appliances are derived from IPS products such as 3Com’s
X-series products.
Others are derived from a combination with firewall products, such as Juniper’s SSG or Cisco’s
Adaptive Security Appliances (ASA). And still others were derived from the ground up as a UTM
appliance such as Fortinet or Astero. The main feature of a UTM is that it includes multiple
security features on one appliance. IPS is merely one feature.
Access Control is also an entirely different security concept. Access control refers to general
rules allowing hosts, users or applications access to specific parts of a network. Typically, access
control helps organizations segment networks and limit access.
While an IPS has the ability to block access to users, hosts or applications, it does so only when
malicious code has been discovered. As such, IPS does not necessarily serve as an access control
device. While it has some access control abilities, firewalls and Network Access Control (NAC)
technologies are better suited to provide these features.
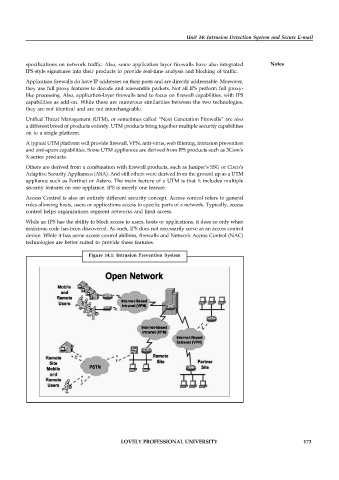
Figure 14.1: Intrusion Prevention System
LOVELY PROFESSIONAL UNIVERSITY 173