Page 42 - DCAP516_COMPUTER_SECURITY
P. 42
Computer Security
Notes To make the security better, need to introduce multiple cipher alphabets, to be used in rotation,
known as poly alphabetic cipher. Like the monoalphabetic cipher, this cipher also has a key,
usually a short, easy to remember word or phrases, rather than a string of 26 distinct character.
Substitution cipher need not always work on one letter at a time. The plain text can be encoded
as two characters at a time where first character indicates the row and second column. The
intersection of the 26 × 26 table is the encrypted value. If 26 different tables are prepared, the
trigrams can be encrypted as units by using the first letter of the each trigram to start a table.
So the units encrypted become longer and larger the cipher text begin to resemble like a ‘Code’.
Cipher encrypts a fixed size unit of plaintext with each operation whereas the code encrypts a
single variable-length linguistic unit, typically a single word or phrase. Breaking a code is like
breaking a giant monoalphabetic cipher. Codes have a disadvantage of requiring large books,
which cannot be replaced easily.
4.1.2 Transposition Ciphers
Substitution ciphers and codes preserve the order of the plaintext but disguise them. Transposition
ciphers, in contrast, record the letters but do not disguise them.
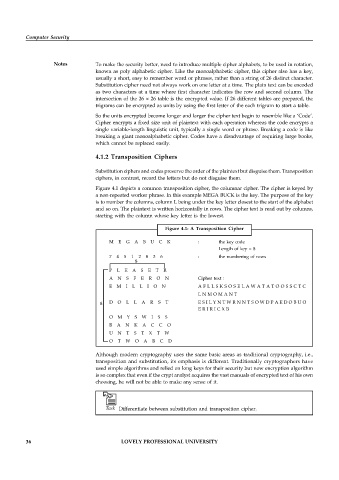
Figure 4.1 depicts a common transposition cipher, the columnar cipher. The cipher is keyed by
a non-repeated worker phrase. In this example MEGA BUCK is the key. The purpose of the key
is to number the columns, column L being under the key letter closest to the start of the alphabet
and so on. The plaintext is written horizontally in rows. The cipher text is read out by columns,
starting with the column whose key letter is the lowest.
Figure 4.1: A Transposition Cipher
M E G A B U C K : the key code
Length of key = 8
7 4 5 1 2 8 3 6 : the numbering of rows
8
P L E A S E T R
A N S F E R O N Cipher text :
E M I L L I O N A F L L S K S O S E L A W A T A T O O S S C T C
L N M O M A N T
8 D O L L A R S T E S I L Y N T W R N N T S O W D P A E D O B U O
E R I R I C X B
O M Y S W I S S
B A N K A C C O
U N T S T X T W
O T W O A B C D
Although modern cryptography uses the same basic areas as traditional cryptography, i.e.,
transposition and substitution, its emphasis is different. Traditionally cryptographers have
used simple algorithms and relied on long keys for their security but now encryption algorithm
is so complex that even if the crypt analyst acquires the vast manuals of encrypted text of his own
choosing, he will not be able to make any sense of it.
Task Differentiate between substitution and transposition cipher.
36 LOVELY PROFESSIONAL UNIVERSITY