Page 48 - DCAP516_COMPUTER_SECURITY
P. 48
Computer Security
Notes In the MixColumns step, each column of the state is multiplied with a fixed polynomial c(x).
In the MixColumns step, the four bytes of each column of the state are combined using an
invertible linear transformation. The MixColumns function takes four bytes as input and outputs
four bytes, where each input byte affects all four output bytes. Together with ShiftRows,
MixColumns provides diffusion in the cipher.
During this operation, each column is multiplied by the known matrix that for the 128 bit key is
The multiplication operation is defined as: multiplication by 1 means leaving unchanged,
multiplication by 2 means shifting byte to the left and multiplication by 3 means shifting to the
left and then performing xor with the initial unshifted value. After shifting, a conditional xor
with 0x1B should be performed if the shifted value is larger than 0xFF.
8
In more general sense, each column is treated as a polynomial over GF(2 ) and is then multiplied
4
3
modulo x +1 with a fixed polynomial c(x) = 0x03 · x + x + x + 0x02. The coefficients are displayed
2
in their hexadecimal equivalent of the binary representation of bit polynomials from GF(2)[x].
The MixColumns step can also be viewed as a multiplication by a particular MDS matrix in a
finite field. This process is described further in the article Rijndael mix columns.
The AddRoundKey Step
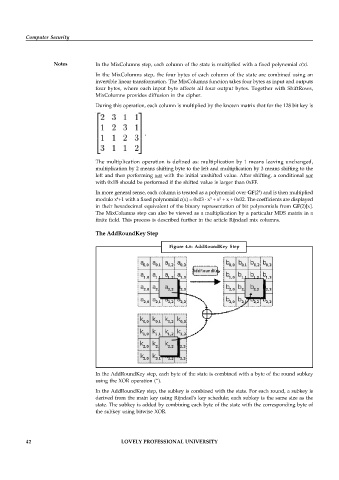
Figure 4.6: AddRoundKey Step
In the AddRoundKey step, each byte of the state is combined with a byte of the round subkey
using the XOR operation (“).
In the AddRoundKey step, the subkey is combined with the state. For each round, a subkey is
derived from the main key using Rijndael’s key schedule; each subkey is the same size as the
state. The subkey is added by combining each byte of the state with the corresponding byte of
the subkey using bitwise XOR.
42 LOVELY PROFESSIONAL UNIVERSITY