Page 65 - DCAP516_COMPUTER_SECURITY
P. 65
Unit 6: User Authentication
because small pieces of related information from different sources can be easily linked together Notes
to form a composite of, for example, a person’s information seeking habits, it is now very
important that individuals are able to maintain control over what information is collected
about them, how it is used, who may use it, and what purpose it is used for.
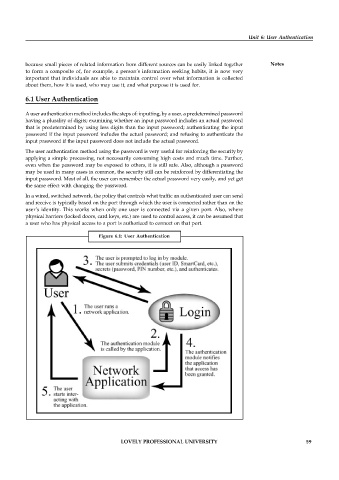
6.1 User Authentication
A user authentication method includes the steps of: inputting, by a user, a predetermined password
having a plurality of digits; examining whether an input password includes an actual password
that is predetermined by using less digits than the input password; authenticating the input
password if the input password includes the actual password; and refusing to authenticate the
input password if the input password does not include the actual password.
The user authentication method using the password is very useful for reinforcing the security by
applying a simple processing, not necessarily consuming high costs and much time. Further,
even when the password may be exposed to others, it is still safe. Also, although a password
may be used in many cases in common, the security still can be reinforced by differentiating the
input password. Most of all, the user can remember the actual password very easily, and yet get
the same effect with changing the password.
In a wired, switched network, the policy that controls what traffic an authenticated user can send
and receive is typically based on the port through which the user is connected rather than on the
user’s identity. This works when only one user is connected via a given port. Also, where
physical barriers (locked doors, card keys, etc.) are used to control access, it can be assumed that
a user who has physical access to a port is authorized to connect on that port.
Figure 6.1: User Authentication
LOVELY PROFESSIONAL UNIVERSITY 59