Page 82 - DCAP516_COMPUTER_SECURITY
P. 82
Computer Security
Notes
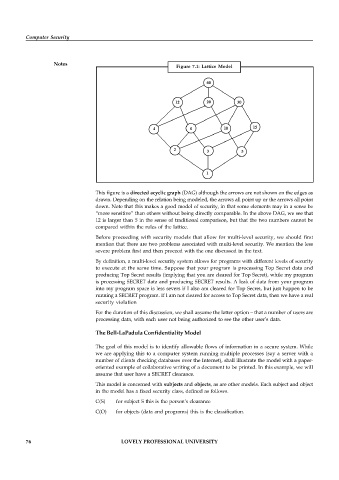
Figure 7.1: Lattice Model
This figure is a directed acyclic graph (DAG) although the arrows are not shown on the edges as
drawn. Depending on the relation being modeled, the arrows all point up or the arrows all point
down. Note that this makes a good model of security, in that some elements may in a sense be
“more sensitive” than others without being directly comparable. In the above DAG, we see that
12 is larger than 5 in the sense of traditional comparison, but that the two numbers cannot be
compared within the rules of the lattice.
Before proceeding with security models that allow for multi-level security, we should first
mention that there are two problems associated with multi-level security. We mention the less
severe problem first and then proceed with the one discussed in the text.
By definition, a multi-level security system allows for programs with different levels of security
to execute at the same time. Suppose that your program is processing Top Secret data and
producing Top Secret results (implying that you are cleared for Top Secret), while my program
is processing SECRET data and producing SECRET results. A leak of data from your program
into my program space is less severs if I also am cleared for Top Secret, but just happen to be
running a SECRET program. If I am not cleared for access to Top Secret data, then we have a real
security violation
For the duration of this discussion, we shall assume the latter option – that a number of users are
processing data, with each user not being authorized to see the other user’s data.
The Bell-LaPadula Confidentiality Model
The goal of this model is to identify allowable flows of information in a secure system. While
we are applying this to a computer system running multiple processes (say a server with a
number of clients checking databases over the Internet), shall illustrate the model with a paper-
oriented example of collaborative writing of a document to be printed. In this example, we will
assume that user have a SECRET clearance.
This model is concerned with subjects and objects, as are other models. Each subject and object
in the model has a fixed security class, defined as follows.
C(S) for subject S this is the person’s clearance
C(O) for objects (data and programs) this is the classification.
76 LOVELY PROFESSIONAL UNIVERSITY