Page 125 - DCAP103_Principle of operating system
P. 125
Principles of Operating Systems
Notes 4.4.4 Mandatory vs. Discretionary Access Control
An example of a discretionary access control is a Unix file—a process or thread can, at its sole
discretion, modify the permissions on a file, thereby permitting access to the file by another
process in the system. Discretionary access controls are useful for some objects in some systems.
An RTOS that is used in a safety- or security-critical system must be able to go one big step
further and provide mandatory access control of critical system objects. For example, consider
an aircraft sensor device, access to which is controlled by a flight control program. The system
designer must be able to set up the system statically such that the flight control program and
only the flight control program has access to this device. Another application in the system
cannot dynamically request and obtain access to this device. And the flight control program
cannot dynamically provide access to the device to any other application in the system. The
access control is enforced by the kernel, is not circumventable by application code, and is thus
mandatory. Mandatory access control provides guarantees. Discretionary access controls are
only as effective as the applications using them, and these applications must be assumed to
have bugs in them.
Differentiate between Mandatory vs. discretionary access control.
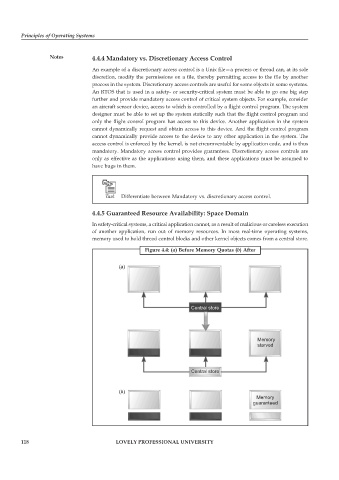
4.4.5 Guaranteed Resource Availability: Space Domain
In safety-critical systems, a critical application cannot, as a result of malicious or careless execution
of another application, run out of memory resources. In most real-time operating systems,
memory used to hold thread control blocks and other kernel objects comes from a central store.
Figure 4.4: (a) Before Memory Quotas (b) After
(a)
Central store
Memory
starved
Central store
(b)
Memory
guaranteed
118 LOVELY PROFESSIONAL UNIVERSITY