Page 229 - DCAP103_Principle of operating system
P. 229
Principles of Operating Systems
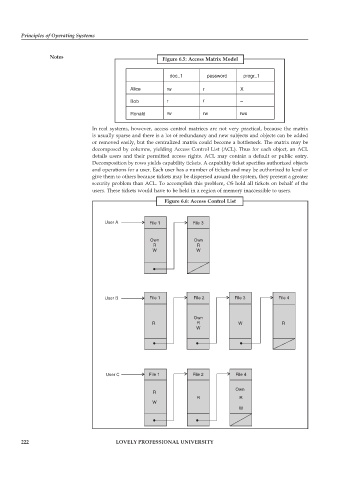
Notes Figure 6.5: Access Matrix Model
In real systems, however, access control matrices are not very practical, because the matrix
is usually sparse and there is a lot of redundancy and new subjects and objects can be added
or removed easily, but the centralized matrix could become a bottleneck. The matrix may be
decomposed by columns, yielding Access Control List (ACL). Thus for each object, an ACL
details users and their permitted access rights. ACL may contain a default or public entry.
Decomposition by rows yields capability tickets. A capability ticket specifies authorized objects
and operations for a user. Each user has a number of tickets and may be authorized to lend or
give them to others because tickets may be dispersed around the system, they present a greater
security problem than ACL. To accomplish this problem, OS hold all tickets on behalf of the
users. These tickets would have to be held in a region of memory inaccessible to users.
Figure 6.6: Access Control List
User A File 1 File 3
Own Own
R R
W W
User B File 1 File 2 File 3 File 4
Own
R R W R
W
User C File 1 File 2 File 4
Own
R
R R
W
W
222 LOVELY PROFESSIONAL UNIVERSITY