Page 276 - DCAP103_Principle of operating system
P. 276
Unit 8: System Protection
8.2 Access Matrix Notes
Access matrices are widely used to hold a symbolic representation of the set of rights available
to subjects for access to objects. In the case of the PO set policy, ‘flow control matrices’ hold
only a single right which determines whether or not flow is permitted from domain to domain,
while more complex policies require more rights, and thus more complex software. Matrices are
well understood data structures which have been used for a long time, and implementations are
very straight forward. The programmer merely implements a table lookup for every protection
related OS request to determine whether or not the requested right is to be granted.
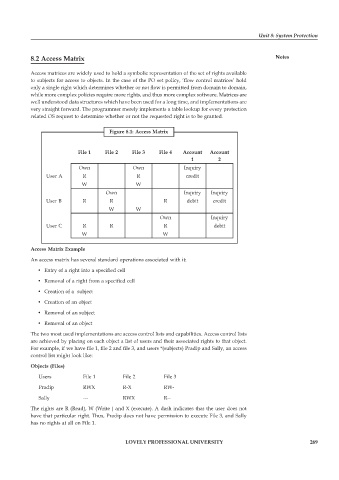
Figure 8.1: Access Matrix
File 1 File 2 File 3 File 4 Account Account
1 2
Own Own Inquiry
User A R R credit
W W
Own Inquiry Inquiry
User B R R R debit credit
W W
Own Inquiry
User C R R R debit
W W
Access Matrix Example
An access matrix has several standard operations associated with it:
• Entry of a right into a specified cell
• Removal of a right from a specified cell
• Creation of a subject
• Creation of an object
• Removal of an subject
• Removal of an object
The two most used implementations are access control lists and capabilities. Access control lists
are achieved by placing on each object a list of users and their associated rights to that object.
For example, if we have file 1, file 2 and file 3, and users *(subjects) Pradip and Sally, an access
control list might look like:
Objects (Files)
Users File 1 File 2 File 3
Pradip RWX R-X RW-
Sally --- RWX R--
The rights are R (Read), W (Write ) and X (execute). A dash indicates that the user does not
have that particular right. Thus, Pradip does not have permission to execute File 3, and Sally
has no rights at all on File 1.
LOVELY PROFESSIONAL UNIVERSITY 269