Page 395 - DCAP103_Principle of operating system
P. 395
Principles of Operating Systems
Notes 13.2.7 File Encryption
Computers are used nowadays to store all kinds of sensitive data, including plans for corporate
takeovers, tax information, etc. where the owners do not especially want revealed to anyone.
Information loss can happen when a laptop computer is lost or stolen, a desktop system is
rebooted using an MS-DOS floppy disk to bypass Windows 2000 security, or a hard disk is
physically removed from one computer and installed on another one with an insecure operating
system. Even the simple act of going to the bathroom and leaving the computer unattended and
logged in can be a huge security breach.
Windows 2000 addresses these problem by having an option to encrypt files, so even in the
event the computer is stolen or rebooted using MS-DOS, the files will be unreadable. The normal
way to use Windows 2000 encryption is to mark certain directories as encrypted, which causes
all the files in them to be encrypted, and new files moved to them or created in them to be
encrypted as well. The actual encryption and decryption is not done by NTFS itself, but by a
driver called EFS (Encrypting File System), which is positioned between NTFS and the user
process. In this way, application programs are unaware of encryption and NTFS itself is only
partially involved in it.
To understand how the encrypting file system works, it is necessary to understand how modern
cryptography works.
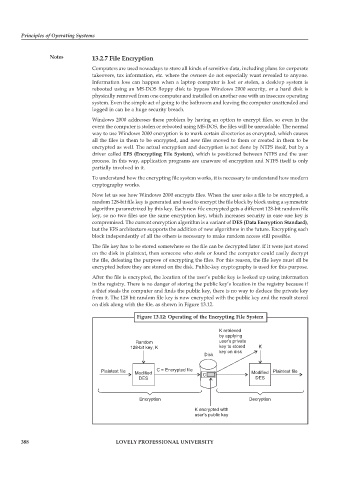
Now let us see how Windows 2000 encrypts files. When the user asks a file to be encrypted, a
random 128-bit file key is generated and used to encrypt the file block by block using a symmetric
algorithm parametrized by this key. Each new file encrypted gets a different 128-bit random file
key, so no two files use the same encryption key, which increases security in ease one key is
compromised. The current encryption algorithm is a variant of DES (Data Encryption Standard),
but the EFS architecture supports the addition of new algorithms in the future. Encrypting each
block independently of all the others is necessary to make random access still possible.
The file key has to be stored somewhere so the file can be decrypted later. If it were just stored
on the disk in plaintext, then someone who stole or found the computer could easily decrypt
the file, defeating the purpose of encrypting the files. For this reason, the file keys must all be
encrypted before they are stored on the disk. Public-key cryptography is used for this purpose.
After the file is encrypted, the location of the user’s public key is looked up using information
in the registry. There is no danger of storing the public key’s location in the registry because if
a thief steals the computer and finds the public key, there is no way to deduce the private key
from it. The 128 bit random file key is now encrypted with the public key and the result stored
on disk along with the file, as shown in Figure 13.12.
Figure 13.12: Operating of the Encrypting File System
K retrieved
by applying
Random user’s private
128-bit key, K key to stored K
key on disk
Disk
Plaintext file Modified C= Encrypted file C Modified Plaintext file
DES DES
Encryption Decryption
K encrypted with
user’s public key
388 LOVELY PROFESSIONAL UNIVERSITY