Page 75 - DCAP104_EXPOSURE_TO_COMPUTER_DISCPLINES
P. 75
Exposure to Computer Disciplines
Notes 4.3.7 Metropolitan Area Network
A Metropolitan area network is a large computer network that usually spans a city or a large
campus.
Sample EPN made of Frame relay WAN connections and dialup remote access.
Sample VPN used to interconnect three offices and remote users.
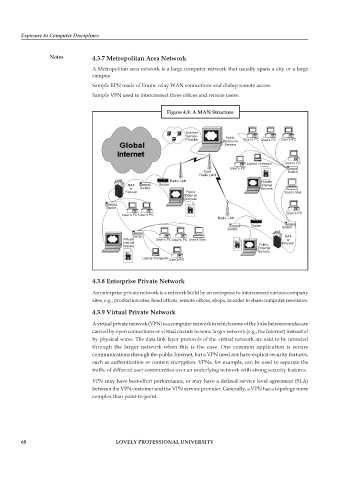
Figure 4.9: A MAN Structure
Internet
Service
Public
Provider Backbone User’s PC User’s PC User’s PC
Servers
Laptop computer User’s PC
User’s PC
Core Switch
Radio LAN
Radio LAN Private
NAT Router Internal
or Switch Servers
Firewall Public User’s Mac
External
Servers
Switch
User’s PC User’s PC User’s PC
Radio LAN
Router
Switch Switch
Switch NAT
Private User’s PC User’s PC User’s Mac or
Internal Public Firewall
Servers External
Servers
Laptop Computer User’s PC
4.3.8 Enterprise Private Network
An enterprise private network is a network build by an enterprise to interconnect various company
sites, e.g., production sites, head offices, remote offices, shops, in order to share computer resources.
4.3.9 Virtual Private Network
A virtual private network (VPN) is a computer network in which some of the links between nodes are
carried by open connections or virtual circuits in some larger network (e.g., the Internet) instead of
by physical wires. The data link layer protocols of the virtual network are said to be tunneled
through the larger network when this is the case. One common application is secure
communications through the public Internet, but a VPN need not have explicit security features,
such as authentication or content encryption. VPNs, for example, can be used to separate the
traffic of different user communities over an underlying network with strong security features.
VPN may have best-effort performance, or may have a defined service level agreement (SLA)
between the VPN customer and the VPN service provider. Generally, a VPN has a topology more
complex than point-to-point.
68 LOVELY PROFESSIONAL UNIVERSITY