Page 107 - DCAP207_NETWORKS_DCAP406_COMPUTER_NETWORKS
P. 107
Computer Networks/Networks
Notes correction mechanism could be set in place. This system would be completely accurate (the odds
of errors being introduced into exactly the same bits in both sets of data are infinitesimally
small), but it would also be insupportably slow. Not only would the transmission time double,
but the time it takes to compare every unit bit by bit must be added.
The concept of including extra information in the transmission solely for the purposes of
comparison is a good one. But instead of repeating the entire data stream, a shorter group of bits
may be appended to the end of each unit. This technique is called redundancy because the extra
bits are redundant to the information: they are discarded as soon as the accuracy of the transmission
has been determined.
Figure shows the process of using-redundant bits to check the accuracy of a data unit. Once the
data stream has been generated, it passes through a device that analyzes it and adds on an
appropriately coded redundancy check: The data unit, now enlarged by several bits, travels over
the link to the receiver. The receiver puts the entire stream through a checking function. If the
received bit stream passes the checking criteria, the data portion of the data unit is accepted and
the redundant bits are discarded.
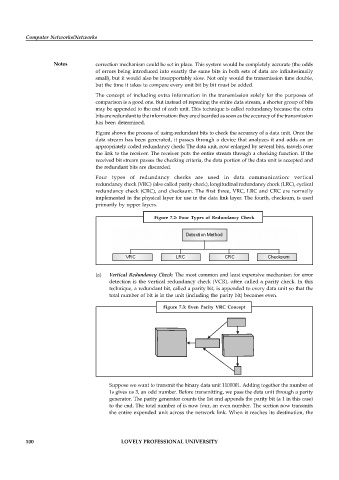
Four types of redundancy checks are used in data communication: vertical
redundancy check (VRC) (also called parity check), longitudinal redundancy check (LRC), cyclical
redundancy check (CRC), and checksum. The first three, VRC, LRC and CRC are normally
implemented in the physical layer for use in the data link layer. The fourth, checksum, is used
primarily by upper layers.
Figure 7.2: Four Types of Redundancy Check
(a) Vertical Redundancy Check: The most common and least expensive mechanism for error
detection is the vertical redundancy check (VCR), often called a parity check. In this
technique, a redundant bit, called a parity bit, is appended to every data unit so that the
total number of bit is in the unit (including the parity bit) becomes even.
Figure 7.3: Even Parity VRC Concept
Suppose we want to transmit the binary data unit 1100001. Adding together the number of
1s gives us 3, an odd number. Before transmitting, we pass the data unit through a parity
generator. The parity generator counts the 1st and appends the parity bit (a 1 in this case)
to the end. The total number of is now four, an even number. The section now transmits
the entire expended unit across the network link. When it reaches its destination, the
100 LOVELY PROFESSIONAL UNIVERSITY