Page 139 - DCAP309_INFORMATION_SECURITY_AND_PRIVACY
P. 139
Unit 9: Firewalls
or proxy. The client then negotiates with the proxy server in order to communicate with the Notes
destination service.
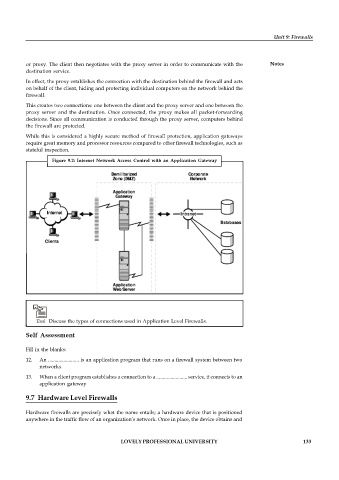
In effect, the proxy establishes the connection with the destination behind the firewall and acts
on behalf of the client, hiding and protecting individual computers on the network behind the
firewall.
This creates two connections: one between the client and the proxy server and one between the
proxy server and the destination. Once connected, the proxy makes all packet-forwarding
decisions. Since all communication is conducted through the proxy server, computers behind
the firewall are protected.
While this is considered a highly secure method of firewall protection, application gateways
require great memory and processor resources compared to other firewall technologies, such as
stateful inspection.
Figure 9.2: Internet Network Access Control with an Application Gateway
Task Discuss the types of connections used in Application Level Firewalls.
Self Assessment
Fill in the blanks:
12. An ........................ is an application program that runs on a firewall system between two
networks.
13. When a client program establishes a connection to a ........................ service, it connects to an
application gateway
9.7 Hardware Level Firewalls
Hardware firewalls are precisely what the name entails; a hardware device that is positioned
anywhere in the traffic flow of an organization’s network. Once in place, the device obtains and
LOVELY PROFESSIONAL UNIVERSITY 133