Page 172 - DCAP309_INFORMATION_SECURITY_AND_PRIVACY
P. 172
Information Security and Privacy
Notes data. The point of measuring performance is to observe the status of considered activities and
facilitate enhancement in those activities by applying counteractive actions, based on observed
dimensions. While a case can be made for using different terms for more comprehensive and
aggregated items, like ‘metrics’ and ‘measures,’ this document accesses these terms
interchangeably.”
“Measurements offer single-point-in-time views of particular, discrete factors, whereas metrics
are derived by comparing to a fixed baseline two or more dimensions taken over time.
Measurements are generated by counting; metrics are produced from analysis. Alternatively,
measurements are objective raw data and metrics are either objective or biased human explanation
of those data.”
For information system security, the procedures are related with aspects of the system that
supply to its security. That is, security metrics engage the application of a method of dimension
to one or more entities of a system that possess an quantifiable security property to attain a
measured value.
Metric Lifecycle
The business logic connected with a metric follows a straightforward dealing out sample:
Create: Obtain primary input data from one or more authoritative providers, including
commercial products or homegrown customer applications.
Calculate: Apply a series of analytic operations (called actions) on the primary data to
derive a result and store the result in the metric results database in the form of one or more
rows in a table.
Communicate: Communicate the metric results in any of the following formats: default
visualization, e-mail notification, e-mail alert based upon detection of some policy
violation.
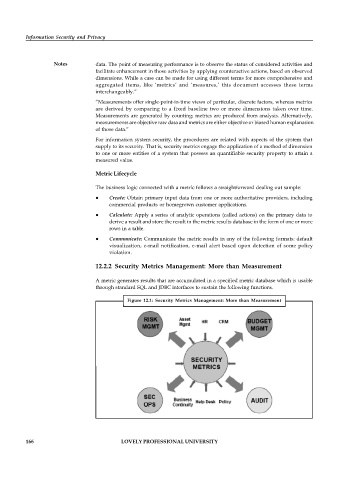
12.2.2 Security Metrics Management: More than Measurement
A metric generates results that are accumulated in a specified metric database which is usable
through standard SQL and JDBC interfaces to sustain the following functions.
Figure 12.1: Security Metrics Management: More than Measurement
166 LOVELY PROFESSIONAL UNIVERSITY