Page 284 - DCAP103_Principle of operating system
P. 284
Unit 8: System Protection
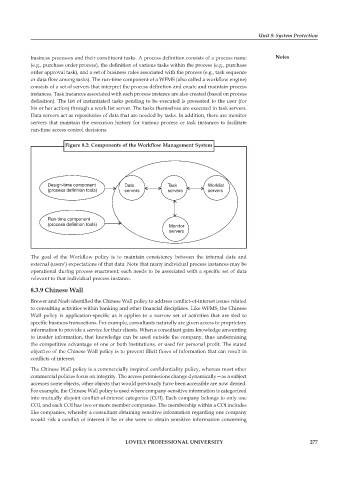
business processes and their constituent tasks. A process definition consists of a process name Notes
(e.g., purchase order process), the definition of various tasks within the process (e.g., purchase
order approval task), and a set of business rules associated with the process (e.g., task sequence
or data flow among tasks). The run-time component of a WFMS (also called a workflow engine)
consists of a set of servers that interpret the process definition and create and maintain process
instances. Task instances associated with each process instance are also created (based on process
definition). The list of instantiated tasks pending to be executed is presented to the user (for
his or her action) through a work list server. The tasks themselves are executed in task servers.
Data servers act as repositories of data that are needed by tasks. In addition, there are monitor
servers that maintain the execution history for various process or task instances to facilitate
run-time access control decisions.
Figure 8.2: Components of the Workflow Management System
The goal of the Workflow policy is to maintain consistency between the internal data and
external (users’) expectations of that data. Note that many individual process instances may be
operational during process enactment; each needs to be associated with a specific set of data
relevant to that individual process instance.
8.3.9 Chinese Wall
Brewer and Nash identified the Chinese Wall policy to address conflict-of-interest issues related
to consulting activities within banking and other financial disciplines. Like WFMS, the Chinese
Wall policy is application-specific as it applies to a narrow set of activities that are tied to
specific business transactions. For example, consultants naturally are given access to proprietary
information to provide a service for their clients. When a consultant gains knowledge amounting
to insider information, that knowledge can be used outside the company, thus undermining
the competitive advantage of one or both institutions, or used for personal profit. The stated
objective of the Chinese Wall policy is to prevent illicit flows of information that can result in
conflicts of interest.
The Chinese Wall policy is a commercially inspired confidentiality policy, whereas most other
commercial policies focus on integrity. The access permissions change dynamically—as a subject
accesses some objects, other objects that would previously have been accessible are now denied.
For example, the Chinese Wall policy is used where company-sensitive information is categorized
into mutually disjoint conflict-of-interest categories (COI). Each company belongs to only one
COI, and each COI has two or more member companies. The membership within a COI includes
like companies, whereby a consultant obtaining sensitive information regarding one company
would risk a conflict of interest if he or she were to obtain sensitive information concerning
LOVELY PROFESSIONAL UNIVERSITY 277