Page 364 - DCAP103_Principle of operating system
P. 364
Unit 12: Processes and Threads in Windows
12.1.6 MS-DOS Emulation Notes
One of the design goals of Windows 2000 was inherited from NT—try to run as many reasonable
MS-DOS programs as possible. This goal is quite different from Windows 98’s stated goal: run
all old MS-DOS programs (to which we add—no matter how ill-behaved they may be).
The way Windows 2000 deals with ancient programs is to run them in a fully protected
environment. When an MS-DOS program is started, a normal Win32 process is started and
loaded with an MS-DOS emulation program, ntvdm(NT Virtual DOS Machine) that will
monitor the MS-DOS program and carry out its system calls. Since MS-DOS only recognized
memory up to 1 MB on the 8088 and only up to 16 MB with bank switching and other tricks
on the 286, it is safe to put ntvdm high in the process’ virtual address space where the
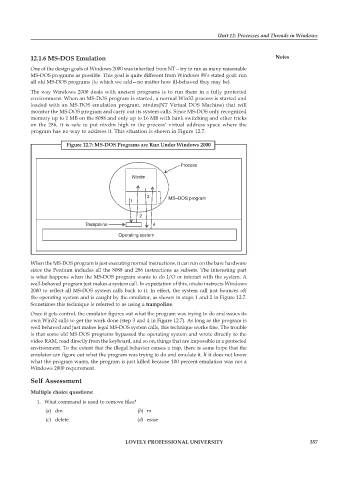
program has no way to address it. This situation is shown in Figure 12.7.
Figure 12.7: MS-DOS Programs are Run Under Windows 2000
When the MS-DOS program is just executing normal instructions, it can run on the bare hardware
since the Pentium includes all the 8088 and 286 instructions as subsets. The interesting part
is what happens when the MS-DOS program wants to do I/O or interact with the system. A
well-behaved program just makes a system call. In expectation of this, ntvdm instructs Windows
2000 to reflect all MS-DOS system calls back to it. In effect, the system call just bounces off
the operating system and is caught by the emulator, as shown in steps 1 and 2 in Figure 12.7.
Sometimes this technique is referred to as using a trampoline.
Once it gets control, the emulator figures out what the program was trying to do and issues its
own Win32 calls to get the work done (step 3 and 4 in Figure 12.7). As long as the program is
well behaved and just makes legal MS-DOS system calls, this technique works fine. The trouble
is that some old MS-DOS programs bypassed the operating system and wrote directly to the
video RAM, read directly from the keyboard, and so on, things that are impossible in a protected
environment. To the extent that the illegal behavior causes a trap, there is some hope that the
emulator can figure out what the program was trying to do and emulate it. If it does not know
what the program wants, the program is just killed because 100 percent emulation was not a
Windows 2000 requirement.
Self Assessment
Multiple choice questions:
1. What command is used to remove files?
( a) dm (b) m
( c) delete (d) erase
LOVELY PROFESSIONAL UNIVERSITY 357