Page 439 - DCAP103_Principle of operating system
P. 439
Principles of Operating Systems
Notes have adopted CTRL-U or some other character. Likewise, to interrupt the running program,
some special key must be hit. Here, too, different users have different preferences. CTRL-C is
a common choice, but it is not universal.
Rather than making a choice and forcing everyone to use it, Linux allows all these special
functions and many others to be customized by the user. A special system call is generally
provided for setting these options. This system call also handles tab expansion, enabling and
disabling of character echoing, conversion between carriage return and line feed, and similar
items. The system call is not permitted on regular files or block special files.
14.5.2 Networking
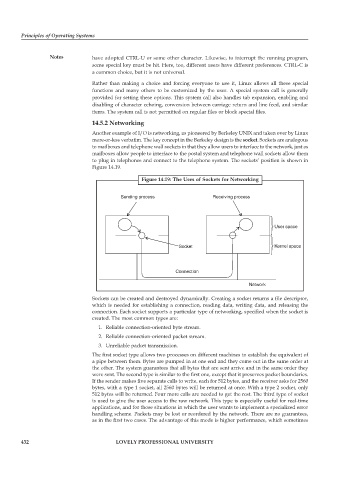
Another example of I/O is networking, as pioneered by Berkeley UNIX and taken over by Linux
more-or-less verbatim. The key concept in the Berkeley design is the socket. Sockets are analogous
to mailboxes and telephone wall sockets in that they allow users to interface to the network, just as
mailboxes allow people to interface to the postal system and telephone wall sockets allow them
to plug in telephones and connect to the telephone system. The sockets’ position is shown in
Figure 14.19.
Figure 14.19: The Uses of Sockets for Networking
Sockets can be created and destroyed dynamically. Creating a socket returns a file descriptor,
which is needed for establishing a connection, reading data, writing data, and releasing the
connection. Each socket supports a particular type of networking, specified when the socket is
created. The most common types are:
1. Reliable connection-oriented byte stream.
2. Reliable connection-oriented packet stream.
3. Unreliable packet transmission.
The first socket type allows two processes on different machines to establish the equivalent of
a pipe between them. Bytes are pumped in at one end and they come out in the same order at
the other. The system guarantees that all bytes that are sent arrive and in the same order they
were sent. The second type is similar to the first one, except that it preserves packet boundaries.
If the sender makes five separate calls to write, each for 512 bytes, and the receiver asks for 2560
bytes, with a type 1 socket, all 2560 bytes will be returned at once. With a type 2 socket, only
512 bytes will be returned. Four more calls are needed to get the rest. The third type of socket
is used to give the user access to the raw network. This type is especially useful for real-time
applications, and for those situations in which the user wants to implement a specialized error
handling scheme. Packets may be lost or reordered by the network. There are no guarantees,
as in the first two cases. The advantage of this mode is higher performance, which sometimes
432 LOVELY PROFESSIONAL UNIVERSITY