Page 233 - Open Soource Technologies 304.indd
P. 233
Unit 9: Web Techniques
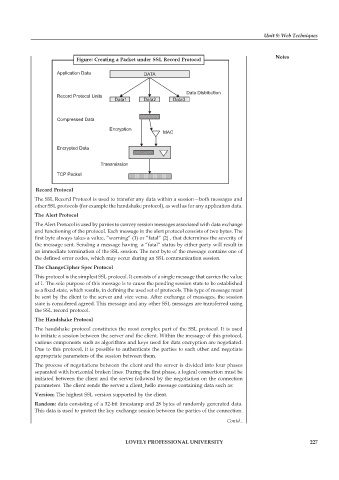
Figure: Creating a Packet under SSL Record Protocol Notes
Application Data DATA
Data Distribution
Record Protocol Units
Data1 Data2 Data3
Compressed Data
Encryption
MAC
Encrypted Data
Transmission
TCP Packet
Record Protocol
The SSL Record Protocol is used to transfer any data within a session—both messages and
other SSL protocols (for example the handshake protocol), as well as for any application data.
The Alert Protocol
The Alert Protocol is used by parties to convey session messages associated with data exchange
and functioning of the protocol. Each message in the alert protocol consists of two bytes. The
first byte always takes a value, “warning” (1) or “fatal” (2) , that determines the severity of
the message sent. Sending a message having a “fatal” status by either party will result in
an immediate termination of the SSL session. The next byte of the message contains one of
the defined error codes, which may occur during an SSL communication session.
The ChangeCipher Spec Protocol
This protocol is the simplest SSL protocol. It consists of a single message that carries the value
of 1. The sole purpose of this message is to cause the pending session state to be established
as a fixed state, which results, in defining the used set of protocols. This type of message must
be sent by the client to the server and vice versa. After exchange of messages, the session
state is considered agreed. This message and any other SSL messages are transferred using
the SSL record protocol.
The Handshake Protocol
The handshake protocol constitutes the most complex part of the SSL protocol. It is used
to initiate a session between the server and the client. Within the message of this protocol,
various components such as algorithms and keys used for data encryption are negotiated.
Due to this protocol, it is possible to authenticate the parties to each other and negotiate
appropriate parameters of the session between them.
The process of negotiations between the client and the server is divided into four phases
separated with horizontal broken lines. During the first phase, a logical connection must be
initiated between the client and the server followed by the negotiation on the connection
parameters. The client sends the server a client_hello message containing data such as:
Version: The highest SSL version supported by the client.
Random: data consisting of a 32-bit timestamp and 28 bytes of randomly generated data.
This data is used to protect the key exchange session between the parties of the connection.
Contd...
LOVELY PROFESSIONAL UNIVERSITY 227