Page 263 - DCAP403_Operating System
P. 263
Operating System
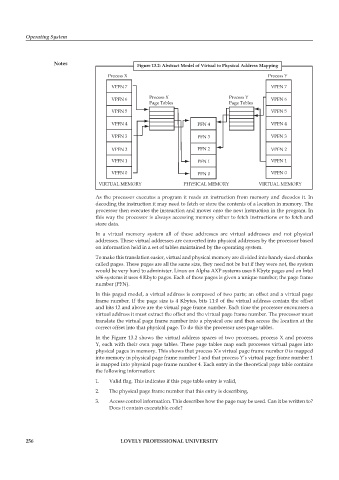
Notes Figure 13.2: Abstract Model of Virtual to Physical Address Mapping
Process X Process Y
VPFN 7 VPFN 7
VPFN 6 Process X Process Y VPFN 6
Page Tables Page Tables
VPFN 5 VPFN 5
VPFN 4 PFN 4 VPFN 4
VPFN 3 PFN 3 VPFN 3
VPFN 2 PFN 2 VPFN 2
VPFN 1 PFN 1 VPFN 1
VPFN 0 PFN 0 VPFN 0
VIRTUAL MEMORY PHYSICAL MEMORY VIRTUAL MEMORY
As the processor executes a program it reads an instruction from memory and decodes it. In
decoding the instruction it may need to fetch or store the contents of a location in memory. The
processor then executes the instruction and moves onto the next instruction in the program. In
this way the processor is always accessing memory either to fetch instructions or to fetch and
store data.
In a virtual memory system all of these addresses are virtual addresses and not physical
addresses. These virtual addresses are converted into physical addresses by the processor based
on information held in a set of tables maintained by the operating system.
To make this translation easier, virtual and physical memory are divided into handy sized chunks
called pages. These pages are all the same size, they need not be but if they were not, the system
would be very hard to administer. Linux on Alpha AXP systems uses 8 Kbyte pages and on Intel
x86 systems it uses 4 Kbyte pages. Each of these pages is given a unique number; the page frame
number (PFN).
In this paged model, a virtual address is composed of two parts; an offset and a virtual page
frame number. If the page size is 4 Kbytes, bits 11:0 of the virtual address contain the offset
and bits 12 and above are the virtual page frame number. Each time the processor encounters a
virtual address it must extract the offset and the virtual page frame number. The processor must
translate the virtual page frame number into a physical one and then access the location at the
correct offset into that physical page. To do this the processor uses page tables.
In the Figure 13.2 shows the virtual address spaces of two processes, process X and process
Y, each with their own page tables. These page tables map each processes virtual pages into
physical pages in memory. This shows that process X’s virtual page frame number 0 is mapped
into memory in physical page frame number 1 and that process Y’s virtual page frame number 1
is mapped into physical page frame number 4. Each entry in the theoretical page table contains
the following information:
1. Valid flag. This indicates if this page table entry is valid,
2. The physical page frame number that this entry is describing,
3. Access control information. This describes how the page may be used. Can it be written to?
Does it contain executable code?
256 LOVELY PROFESSIONAL UNIVERSITY