Page 51 - DCAP403_Operating System
P. 51
Operating System
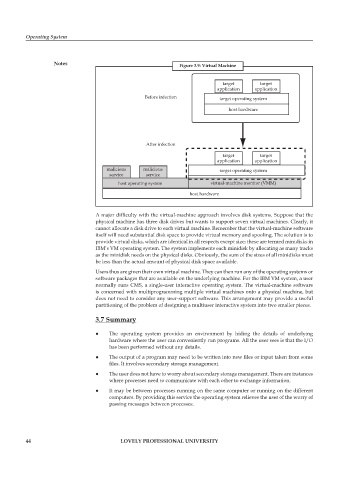
Notes Figure 3.9: Virtual Machine
target target
application application
Before infection target operating system
host hardware
After infection
target target
application application
malicious malicious target operating system
service service
host operating system virtual-machine monitor (VMM)
host hardware
A major difficulty with the virtual-machine approach involves disk systems. Suppose that the
physical machine has three disk drives but wants to support seven virtual machines. Clearly, it
cannot allocate a disk drive to each virtual machine. Remember that the virtual-machine software
itself will need substantial disk space to provide virtual memory and spooling. The solution is to
provide virtual disks, which are identical in all respects except size; these are termed minidisks in
IBM’s VM operating system. The system implements each minidisk by allocating as many tracks
as the minidisk needs on the physical disks. Obviously, the sum of the sizes of all minidisks must
be less than the actual amount of physical disk space available.
Users thus are given their own virtual machine. They can then run any of the operating systems or
software packages that are available on the underlying machine. For the IBM VM system, a user
normally runs CMS, a single-user interactive operating system. The virtual-machine software
is concerned with multiprogramming multiple virtual machines onto a physical machine, but
does not need to consider any user-support software. This arrangement may provide a useful
partitioning of the problem of designing a multiuser interactive system into two smaller pieces.
3.7 Summary
The operating system provides an environment by hiding the details of underlying
hardware where the user can conveniently run programs. All the user sees is that the I/O
has been performed without any details.
The output of a program may need to be written into new files or input taken from some
files. It involves secondary storage management.
The user does not have to worry about secondary storage management. There are instances
where processes need to communicate with each other to exchange information.
It may be between processes running on the same computer or running on the different
computers. By providing this service the operating system relieves the user of the worry of
passing messages between processes.
44 LOVELY PROFESSIONAL UNIVERSITY