Page 225 - DCAP406_DCAP_207_Computer Networks
P. 225
Computer Networks/Networks
Notes is to perform a columnar transposition on the ordinary alphabet using the keyword, but this is
not often done.
Although the number of possible keys is very large (26! H” 288.4, or about 88 bits), this cipher is
not very strong, being easily broken. Provided the message is of reasonable length, the
cryptanalyst can deduce the probable meaning of the most common symbols by analyzing the
frequency distribution of the ciphertext—frequency analysis. This allows formation of partial
words, which can be tentatively filled in, progressively expanding the (partial) solution (see
frequency analysis for a demonstration of this). In some cases, underlying words can also be
determined from the pattern of their letters; for example, attract, osseous, and words with those
two as the root are the only common English words with the pattern ABBCADB. Many people
solve such ciphers for recreation, as with cryptogram puzzles in the newspaper.
Notes According to the unicity distance of English, 27.6 letters of ciphertext are required
to crack a mixed alphabet simple substitution. In practice, typically about 50 letters are
needed, although some messages can be broken with fewer if unusual patterns are found.
In other cases, the plaintext can be contrived to have a nearly flat frequency distribution,
and much longer plaintexts will then be required by the user.
14.5.2 Transposition Cipher
In cryptography, a transposition cipher is a method of encryption by which the positions held
by units of plaintext (which are commonly characters or groups of characters) are shifted according
to a regular system, so that the ciphertext constitutes a permutation of the plaintext. That is, the
order of the units is changed. Mathematically a bijective function is used on the characters’
positions to encrypt and an inverse function to decrypt.
Following are some implementations:
Transposition ciphers encrypt plaintext by moving small pieces of the message around. Anagrams
are a primitive transposition cipher.
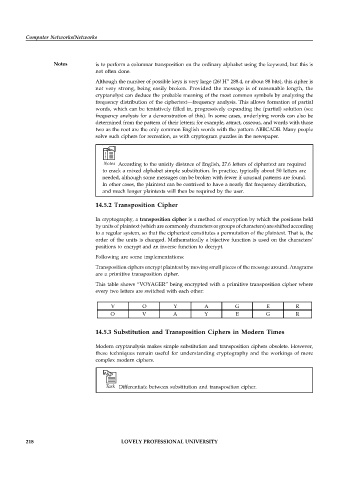
This table shows “VOYAGER” being encrypted with a primitive transposition cipher where
every two letters are switched with each other:
V O Y A G E R
O V A Y E G R
14.5.3 Substitution and Transposition Ciphers in Modern Times
Modern cryptanalysis makes simple substitution and transposition ciphers obsolete. However,
these techniques remain useful for understanding cryptography and the workings of more
complex modern ciphers.
Task Differentiate between substitution and transposition cipher.
218 LOVELY PROFESSIONAL UNIVERSITY