Page 99 - DCAP508_DATABASE_ADMINISTRATION
P. 99
Unit 6: SQL Server Authentication
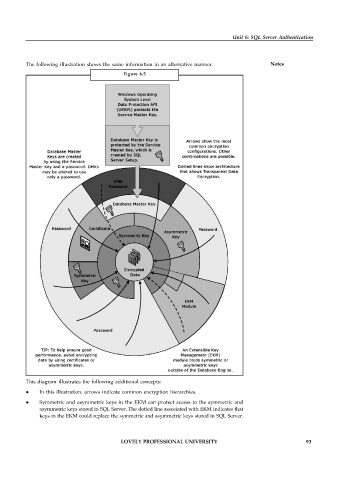
The following illustration shows the same information in an alternative manner. Notes
Figure 6.5
This diagram illustrates the following additional concepts:
In this illustration, arrows indicate common encryption hierarchies.
Symmetric and asymmetric keys in the EKM can protect access to the symmetric and
asymmetric keys stored in SQL Server. The dotted line associated with EKM indicates that
keys in the EKM could replace the symmetric and asymmetric keys stored in SQL Server.
LOVELY PROFESSIONAL UNIVERSITY 93