Page 115 - DCAP311_DCAP607_WIRELESS_NETWORKS
P. 115
Unit 7: Wireless LAN
WLAN data transfer in itself is implemented by one of the following technologies: Notes
1. Frequency Hopping Spread Spectrum: Frequency Hopping Spread Spectrum (FHSS) uses
a narrowband carrier that changes frequency in a pattern known to both transmitter and
receiver. Properly synchronized, the net effect is to maintain a single logical channel. To an
unintended receiver, FHSS appears to be short-duration impulse noise.
2. Direct Sequence Spread Spectrum: Direct Sequence Spread Spectrum (DSSS) generates a
redundant bit pattern for each bit to be transmitted. This bit pattern is called a chip (or
chipping code). The longer the chip, the greater the probability that the original data can
be recovered (the more bandwidth required also). Even if one or more bits in the chip are
damaged during transmission, statistical techniques can recover the original data without
the need for retransmission. To an unintended receiver, DSSS appears as low-power
wideband noise and is ignored by most narrowband receivers.
3. Infrared Technology: Infrared (IR) systems use very high frequencies, just below visible
light in the electromagnetic spectrum, to carry data. Like light, IR cannot penetrate opaque
objects; it is either directed (line-of-sight) or diffuse technology. Inexpensive directed
systems provide very limited range (3 ft) and are occasionally used in specific WLAN
applications. High performance directed IR is impractical for mobile users and is therefore
used only to implement fixed subnetworks. Diffuse (or reflective) IR WLAN systems do
not require line-of-sight, but cells are limited to individual rooms.
7.2.4 Wireless LAN Configurations
In hot spots such as airport and coffee shops, some users need to access the Internet through
WLAN. In this case, if user authentication cannot be performed, unauthorized users are able
to use network resources, which may occupy wireless channels to increase bandwidth cost,
decrease the service quality for authorized users, and bring losses to wireless service providers.
Used together with IEEE 802.11i, RADIUS authentication and accounting, wireless user isolation
can provide security protection for users.
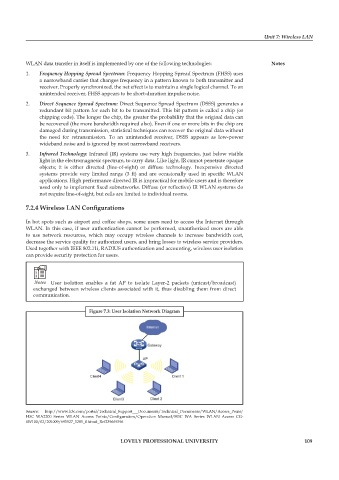
Notes User isolation enables a fat AP to isolate Layer-2 packets (unicast/broadcast)
exchanged between wireless clients associated with it, thus disabling them from direct
communication.
Figure 7.3: User Isolation Network Diagram
Source: http://www.h3c.com/portal/Technical_Support___Documents/Technical_Documents/WLAN/Access_Point/
H3C_WA2200_Series_WLAN_Access_Points/Configuration/Operation_Manual/H3C_WA_Series_WLAN_Access_CG-
6W100/02/201009/691527_1285_0.htm#_Ref239669396
LOVELY PROFESSIONAL UNIVERSITY 109