Page 192 - DCAP403_Operating System
P. 192
Unit 10: System Protection
Notes
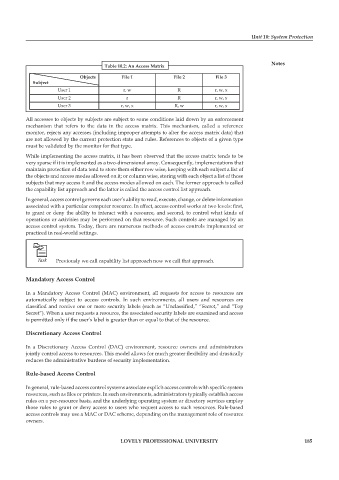
Table 10.2: An Access Matrix
Objects File 1 File 2 File 3
Subject
User 1 r, w R r, w, x
User 2 r R r, w, x
User 3 r, w, x R, w r, w, x
All accesses to objects by subjects are subject to some conditions laid down by an enforcement
mechanism that refers to the data in the access matrix. This mechanism, called a reference
monitor, rejects any accesses (including improper attempts to alter the access matrix data) that
are not allowed by the current protection state and rules. References to objects of a given type
must be validated by the monitor for that type.
While implementing the access matrix, it has been observed that the access matrix tends to be
very sparse if it is implemented as a two-dimensional array. Consequently, implementations that
maintain protection of data tend to store them either row wise, keeping with each subject a list of
the objects and access modes allowed on it; or column wise, storing with each object a list of those
subjects that may access it and the access modes allowed on each. The former approach is called
the capability list approach and the latter is called the access control list approach.
In general, access control governs each user’s ability to read, execute, change, or delete information
associated with a particular computer resource. In effect, access control works at two levels: fi rst,
to grant or deny the ability to interact with a resource, and second, to control what kinds of
operations or activities may be performed on that resource. Such controls are managed by an
access control system. Today, there are numerous methods of access controls implemented or
practiced in real-world settings.
Task Previously we call capability list approach now we call that approach.
Mandatory Access Control
In a Mandatory Access Control (MAC) environment, all requests for access to resources are
automatically subject to access controls. In such environments, all users and resources are
classified and receive one or more security labels (such as “Unclassified,” “Secret,” and “Top
Secret”). When a user requests a resource, the associated security labels are examined and access
is permitted only if the user’s label is greater than or equal to that of the resource.
Discretionary Access Control
In a Discretionary Access Control (DAC) environment, resource owners and administrators
jointly control access to resources. This model allows for much greater flexibility and drastically
reduces the administrative burdens of security implementation.
Rule-based Access Control
In general, rule-based access control systems associate explicit access controls with specifi c system
resources, such as files or printers. In such environments, administrators typically establish access
rules on a per-resource basis, and the underlying operating system or directory services employ
those rules to grant or deny access to users who request access to such resources. Rule-based
access controls may use a MAC or DAC scheme, depending on the management role of resource
owners.
LOVELY PROFESSIONAL UNIVERSITY 185