Page 46 - DCAP403_Operating System
P. 46
Unit 3: Operating System Structure
An exokernel employs three techniques to export resources securely: Notes
1. By using secure bindings, applications can securely bind to machine resources and handle
events.
2. By using visible re-source revocation, applications participate in a resource revocation
protocol.
3. By using an abort protocol, an exokernel can break secure bindings of uncooperative
applications by force.
The advantages of exokernel systems among others are:
1. Exokernels can be made efficient due to the limited number of simple primitives they must
provide
2. Low-level secure multiplexing of hardware resources can be provided with low overhead
3. Traditional abstractions, such as VM and IPC, can be implemented efficiently at application
level, where they can be easily extended, specialized, or replaced
4. Applications can create special-purpose implementations of abstractions, tailored to their
functionality and performance needs.
Finally, many of the hardware resources in microkernel systems, such as the network, screen, and
disk, are encapsulated in heavyweight servers that cannot be bypassed or tailored to application-
specific needs. These heavyweight servers can be viewed as fixed kernel subsystems that run in
user-space.
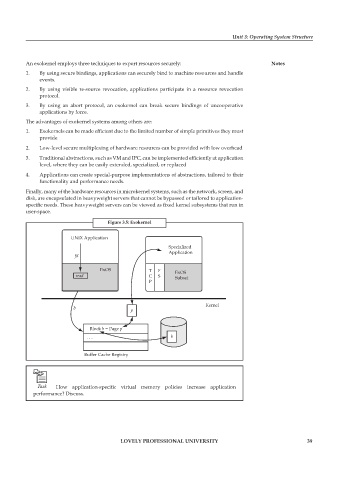
Figure 3.5: Exokernel
UNIX Application
Specialized
Application
fd
ExOS T F ExOS
read C S Subset
P
Kernel
b p
Block b = Page p
. . . b
Buffer Cache Registry
Task How application-specific virtual memory policies increase application
performance? Discuss.
LOVELY PROFESSIONAL UNIVERSITY 39