Page 186 - DCAP304_DCAP515_SOFTWARE_PROJECT_MANAGEMENT
P. 186
Software Project Management
Notes In businesses, risk management entails organized activity to manage uncertainty and threats
and involves people following procedures and using tools in order to ensure conformance with
risk-management policies.
Risk management is also used in the public sector to identify and mitigate risk to critical
infrastructure. For the most part, these methodologies consist of the following elements,
performed, more or less, in the following order:
1. identify assets and identify which are most critical
2. identify, characterize, and assess threats
3. assess the vulnerability of critical assets to specific threats
4. determine the risk (i.e. the expected consequences of specific types of attacks on specific assets)
5. identify ways to reduce those risks
6. prioritize risk reduction measures based on a strategy.
The strategies include transferring the risk to another party, avoiding the risk, reducing the
negative effect of the risk, and accepting some or all of the consequences of a particular risk.
Example: Example of risk management:
High impact risk areas for the International Space Station.
10.1.1 What is Risk?
Risk is defined as “The possibility of suffering harm or loss; danger.” Even if we’re not recognizable
with the formal definition, most of us have an innate sense of risk. We are aware of the potential
dangers that permeate even simple daily activities, from getting injured when crossing the street
to having a heart attack because our cholesterol level is too high. Although we prefer not to dwell
on the myriad of hazards that surround us, these risks shape many of our behaviors. Experience (or
a parent) has taught us to look both ways before stepping off the curb and most of us at least think
twice before ordering a steak. Indeed, we manage personal risks every day.
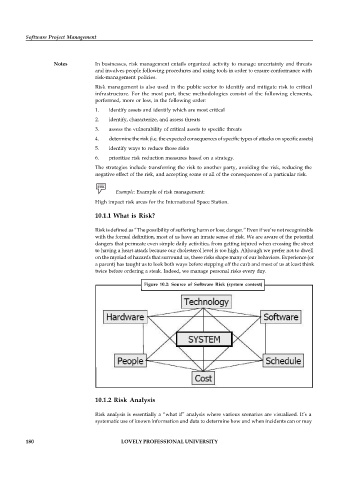
Figure 10.2: Source of Software Risk (system context)
10.1.2 Risk Analysis
Risk analysis is essentially a “what if” analysis where various scenarios are visualized. It’s a
systematic use of known information and data to determine how and when incidents can or may
180 LOVELY PROFESSIONAL UNIVERSITY