Page 136 - DCAP309_INFORMATION_SECURITY_AND_PRIVACY
P. 136
Information Security and Privacy
Notes Traditional DMZs permit computers behind the firewall to start requests outbound to the DMZ.
Computers in the DMZ in turn respond, forward or reissue needs out to the Internet or other
public network, as proxy servers do. Many DMZ implementations, actually, simply utilize a
proxy server or servers as the computers inside the DMZ. The LAN firewall, however, averts
computers in the DMZ from commencing inbound requests.
DMZ is a generally-touted trait of home broadband routers. Though, in most instances these
traits are not true DMZs. Broadband routers frequently implement a DMZ just through additional
firewall rules, signifying that incoming requests arrive at the firewall directly.
!
Caution In a true DMZ, incoming requests must first pass via a DMZ computer before
attaining the firewall.
Self Assessment
Fill in the blanks:
4. ........................ is a firewall configuration for protecting local area networks (LANs).
5. Computers in the DMZ in turn respond, forward or reissue needs out to the Internet or
other public network, as ........................ do.
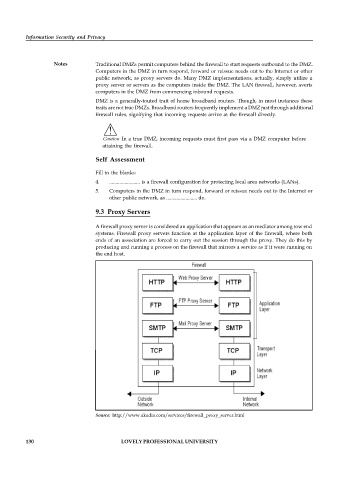
9.3 Proxy Servers
A firewall proxy server is considered an application that appears as an mediator among tow end
systems. Firewall proxy servers function at the application layer of the firewall, where both
ends of an association are forced to carry out the session through the proxy. They do this by
producing and running a process on the firewall that mirrors a service as if it were running on
the end host.
Source: http://www.akadia.com/services/firewall_proxy_server.html
130 LOVELY PROFESSIONAL UNIVERSITY