Page 167 - DCAP402_DCAO204_DATABASE MANAGEMENT SYSTEM_MANAGING DATABASE
P. 167
Database Management Systems/Managing Database
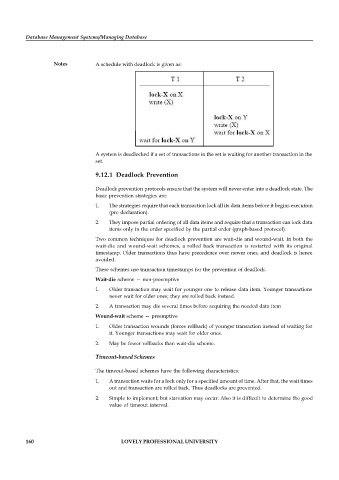
Notes A schedule with deadlock is given as:
A system is deadlocked if a set of transactions in the set is waiting for another transaction in the
set.
9.12.1 Deadlock Prevention
Deadlock prevention protocols ensure that the system will never enter into a deadlock state. The
basic prevention strategies are:
1. The strategies require that each transaction lock all its data items before it begins execution
(pre declaration).
2. They impose partial ordering of all data items and require that a transaction can lock data
items only in the order specified by the partial order (graph-based protocol).
Two common techniques for deadlock prevention are wait-die and wound-wait. In both the
wait-die and wound-wait schemes, a rolled back transaction is restarted with its original
timestamp. Older transactions thus have precedence over newer ones, and deadlock is hence
avoided.
These schemes use transaction timestamps for the prevention of deadlock.
Wait-die scheme — non-preemptive
1. Older transaction may wait for younger one to release data item. Younger transactions
never wait for older ones; they are rolled back instead.
2. A transaction may die several times before acquiring the needed data item
Wound-wait scheme — preemptive
1. Older transaction wounds (forces rollback) of younger transaction instead of waiting for
it. Younger transactions may wait for older ones.
2. May be fewer rollbacks than wait-die scheme.
Timeout-based Schemes
The timeout-based schemes have the following characteristics:
1. A transaction waits for a lock only for a specified amount of time. After that, the wait times
out and transaction are rolled back. Thus deadlocks are prevented.
2. Simple to implement; but starvation may occur. Also it is difficult to determine the good
value of timeout interval.
160 LOVELY PROFESSIONAL UNIVERSITY