Page 196 - DCAP402_DCAO204_DATABASE MANAGEMENT SYSTEM_MANAGING DATABASE
P. 196
Unit 11: Recovery System
Notes
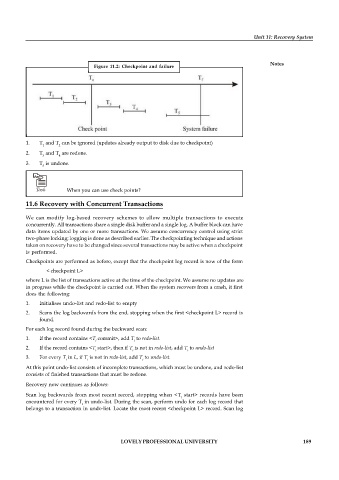
Figure 11.2: Checkpoint and failure
1. T and T can be ignored (updates already output to disk due to checkpoint)
1 2
2. T and T are redone.
3 4
3. T is undone.
5
Task When you can use check points?
11.6 Recovery with Concurrent Transactions
We can modify log-based recovery schemes to allow multiple transactions to execute
concurrently. All transactions share a single disk buffer and a single log. A buffer block can have
data items updated by one or more transactions. We assume concurrency control using strict
two-phase locking; logging is done as described earlier. The checkpointing technique and actions
taken on recovery have to be changed since several transactions may be active when a checkpoint
is performed.
Checkpoints are performed as before, except that the checkpoint log record is now of the form
< checkpoint L>
where L is the list of transactions active at the time of the checkpoint. We assume no updates are
in progress while the checkpoint is carried out. When the system recovers from a crash, it first
does the following:
1. Initialises undo-list and redo-list to empty
2. Scans the log backwards from the end, stopping when the first <checkpoint L> record is
found.
For each log record found during the backward scan:
1. If the record contains <T commit>, add T to redo-list.
i i
2. If the record contains <T start>, then if T is not in redo-list, add T to undo-list
i i i
3. For every T in L, if T is not in redo-list, add T to undo-list.
i i i
At this point undo-list consists of incomplete transactions, which must be undone, and redo-list
consists of finished transactions that must be redone.
Recovery now continues as follows:
Scan log backwards from most recent record, stopping when <T start> records have been
i
encountered for every T in undo-list. During the scan, perform undo for each log record that
i
belongs to a transaction in undo-list. Locate the most recent <checkpoint L> record. Scan log
LOVELY PROFESSIONAL UNIVERSITY 189