Page 154 - DCAP516_COMPUTER_SECURITY
P. 154
Computer Security
Notes (ii) to lure an attacker to a place in which you may be able to learn enough to identify
and stop the attacker
(iii) to provide an attractive but diversionary playground, hoping that the attacker will
leave your real system alone.
A honeypot has no special features. It is just a computer system or a network segment,
loaded with servers and devices and data. It may be protected with a firewall, although
you want the attackers to have some access. There may be some monitoring capability,
done carefully so that the monitoring is not evident to the attacker.
12. Traffic Flow Security: So far, we have looked at controls that cover the most common
network threats: cryptography for eavesdropping, authentication methods for
impersonation, intrusion detection systems for attacks in progress, architecture for structural
flaws. Earlier in this book, we listed threats, including a threat of traffic flow inference. If
the attacker can detect an exceptional volume of traffic between two points, the attacker
may infer the location of an event about to occur.
The countermeasure to traffic flow threats is to disguise the traffic flow. One way to
disguise traffic flow, albeit costly and perhaps crude, is to ensure a steady volume of traffic
between two points. If traffic between A and B is encrypted so that the attacker can detect
only the number of packets flowing, A and B can agree to pass recognizable (to them) but
meaningless encrypted traffic. When A has much to communicate to B, there will be few
meaningless packets; when communication is light, A will pad the traffic stream with
many spurious packets.
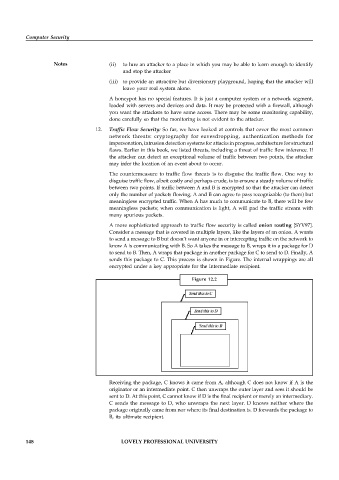
A more sophisticated approach to traffic flow security is called onion routing [SYV97].
Consider a message that is covered in multiple layers, like the layers of an onion. A wants
to send a message to B but doesn’t want anyone in or intercepting traffic on the network to
know A is communicating with B. So A takes the message to B, wraps it in a package for D
to send to B. Then, A wraps that package in another package for C to send to D. Finally, A
sends this package to C. This process is shown in Figure. The internal wrappings are all
encrypted under a key appropriate for the intermediate recipient.
Figure 12.2
Receiving the package, C knows it came from A, although C does not know if A is the
originator or an intermediate point. C then unwraps the outer layer and sees it should be
sent to D. At this point, C cannot know if D is the final recipient or merely an intermediary.
C sends the message to D, who unwraps the next layer. D knows neither where the
package originally came from nor where its final destination is. D forwards the package to
B, its ultimate recipient.
148 LOVELY PROFESSIONAL UNIVERSITY