Page 185 - DCAP516_COMPUTER_SECURITY
P. 185
Unit 14: Intrusion Detection System and Secure E-mail
An IDS will flag the events and alert an administrator. The administrator can then see what is Notes
happening right after or even while the attacks are still taking place. This gives an administrator
the advantage of being able to analyze the techniques being used, source of attacks, and methods
used by the hacker.
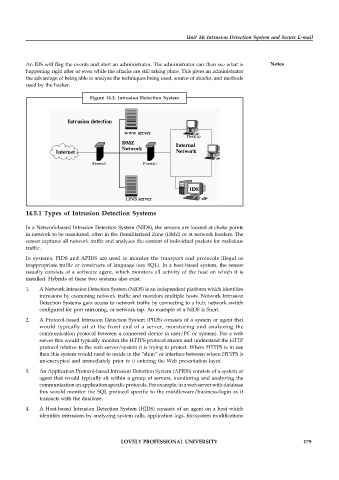
Figure 14.2: Intrusion Detection System
14.5.1 Types of Intrusion Detection Systems
In a Network-based Intrusion Detection System (NIDS), the sensors are located at choke points
in network to be monitored, often in the Demilitarized Zone (DMZ) or at network borders. The
sensor captures all network traffic and analyzes the content of individual packets for malicious
traffic.
In systems, PIDS and APIDS are used to monitor the transport and protocols illegal or
inappropriate traffic or constructs of language (say SQL). In a host-based system, the sensor
usually consists of a software agent, which monitors all activity of the host on which it is
installed. Hybrids of these two systems also exist.
1. A Network Intrusion Detection System (NIDS) is an independent platform which identifies
intrusions by examining network traffic and monitors multiple hosts. Network Intrusion
Detection Systems gain access to network traffic by connecting to a hub, network switch
configured for port mirroring, or network tap. An example of a NIDS is Snort.
2. A Protocol-based Intrusion Detection System (PIDS) consists of a system or agent that
would typically sit at the front end of a server, monitoring and analyzing the
communication protocol between a connected device (a user/PC or system). For a web
server this would typically monitor the HTTPS protocol stream and understand the HTTP
protocol relative to the web server/system it is trying to protect. Where HTTPS is in use
then this system would need to reside in the “shim” or interface between where HTTPS is
un-encrypted and immediately prior to it entering the Web presentation layer.
3. An Application Protocol-based Intrusion Detection System (APIDS) consists of a system or
agent that would typically sit within a group of servers, monitoring and analyzing the
communication on application specific protocols. For example; in a web server with database
this would monitor the SQL protocol specific to the middleware/business-login as it
transacts with the database.
4. A Host-based Intrusion Detection System (HIDS) consists of an agent on a host which
identifies intrusions by analyzing system calls, application logs, file-system modifications
LOVELY PROFESSIONAL UNIVERSITY 179