Page 80 - DCAP306_DCAP511_E-COMMERCE_AND_E-BUSINESS
P. 80
Unit 6: Security Framework
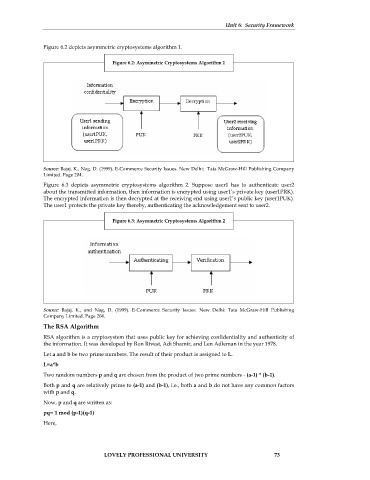
Figure 6.2 depicts asymmetric cryptosystems algorithm 1.
Figure 6.2: Asymmetric Cryptosystems Algorithm 1
Source: Bajaj. K., Nag. D. (1999). E-Commerce Security Issues. New Delhi: Tata McGraw-Hill Publishing Company
Limited. Page 204.
Figure 6.3 depicts asymmetric cryptosystems algorithm 2. Suppose user1 has to authenticate user2
about the transmitted information, then information is encrypted using user1’s private key (user1PRK).
The encrypted information is then decrypted at the receiving end using user1’s public key (user1PUK).
The user1 protects the private key thereby, authenticating the acknowledgement sent to user2.
Figure 6.3: Asymmetric Cryptosystems Algorithm 2
Source: Bajaj, K., and Nag, D. (1999). E-Commerce Security Issues. New Delhi: Tata McGraw-Hill Publishing
Company Limited. Page 204.
The RSA Algorithm
RSA algorithm is a cryptosystem that uses public key for achieving confidentiality and authenticity of
the information. It was developed by Ron Rivest, Adi Shamir, and Len Adleman in the year 1978.
Let a and b be two prime numbers. The result of their product is assigned to L.
L=a*b
Two random numbers p and q are chosen from the product of two prime numbers - (a-1) * (b-1).
Both p and q are relatively prime to (a-1) and (b-1), i.e., both a and b do not have any common factors
with p and q.
Now, p and q are written as:
pq= 1 mod (p-1)(q-1)
Here,
LOVELY PROFESSIONAL UNIVERSITY 73