Page 119 - DCAP309_INFORMATION_SECURITY_AND_PRIVACY
P. 119
Unit 8: Cryptography and Encryption
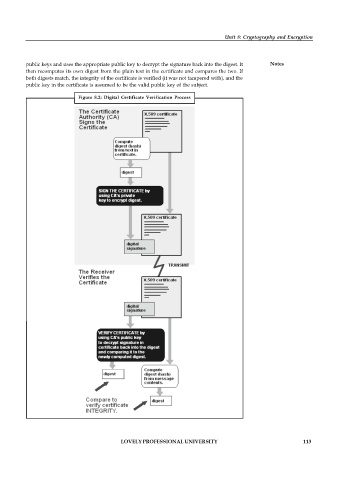
public keys and uses the appropriate public key to decrypt the signature back into the digest. It Notes
then recomputes its own digest from the plain text in the certificate and compares the two. If
both digests match, the integrity of the certificate is verified (it was not tampered with), and the
public key in the certificate is assumed to be the valid public key of the subject.
Figure 8.2: Digital Certificate Verification Process
LOVELY PROFESSIONAL UNIVERSITY 113