Page 121 - DCAP309_INFORMATION_SECURITY_AND_PRIVACY
P. 121
Unit 8: Cryptography and Encryption
The idea is similar to asymmetric cryptography but it is complimentary. Whereas in public-key Notes
encryption schemes, the public key is used to encrypt the message and the private key to
decrypt, digital signatures are obtained generating a number using the private key and verified
with the public key.
Digital signatures have many applications in information security, including authentication,
data integrity and non-repudiation. One of the most significant applications of digital signatures
is the certification of public keys in large networks.
Certification is a means for a Trusted Third Party (TTP) to bind the identity of a user to a public
key, so that at some later time, other entities can authenticate a public key without assistance
from a trusted third party. It now becomes clear how asymmetric cryptography surmounts the
key distribution problem. A user, destined to receive an encrypted message, can send his
certificate containing his public key issued by a TTL or Certificate Authority. The receiver, who
desires to encrypt and send the message, can authenticate that the certificate was issued by the
common Certificate Authority (CA) using the CA public key thus acquiring the guaranty that
the public key received belongs to the intended recipient (or at least the CA’s guaranty).
The first method discovered was the RSA signature scheme (an RSA public key encryption
compliment scheme) and is still widely used in Internet together with another digital scheme
called Digital Signature Algorithm (DSA) proposed by the National Institute of Standards and
Technology (NIST) and is the first digital signature scheme to be recognized by any government
(1991).
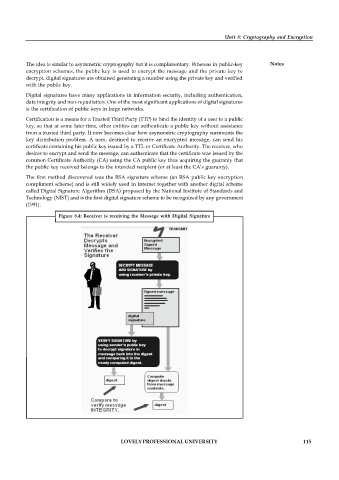
Figure 8.4: Receiver is receiving the Message with Digital Signature
LOVELY PROFESSIONAL UNIVERSITY 115