Page 29 - DCAP309_INFORMATION_SECURITY_AND_PRIVACY
P. 29
Unit 2: Threats
passwords and administrator password times to trace back to
other data command information Correlate user perpetrator Notes
functions, System problem
indicating administrator reports
multiple printouts of relevant to
Masquerades user logs possible
Masquerades
Browsing Application Usually Authorized user "Finger" type Destroy Correlate user Change user
Network automated found online at services discarded identification password or use
scanning of large unusual or off- provide media with shift standard
quantities of shift hours, information to When on open times or administrator
unprotected data indicating a any and all source increased functions to
(discarded possible users. networks frequency of determine access
media or online Masquerade The especially, access point, then trace
"finger" type Authorized user information is disable Correlate user back to
commands) to attempting usually "finger" type command logs perpetrator
obtain clues as to administrator assumed safe services with
how to achieve command but can give administrator
access functions clues to command
passwords functions
(e.g., spouse’s
name)
Spamming Spamming Application Overloading a Repeated system Open source Require Monitor disk Analyze message
Network system with crashes, networks authentication partitions, headers to
incoming eventually traced especially fields in network attempt trace
message or other to overfull buffer vulnerable message traffic sockets, etc. back to
traffic to cause or swap space for overfull perpetrator
system crashes conditions
Tunneling Tunneling Network Any digital Bizarre system Tunneling Design Changes in Patch or replace
attack that behaviors such attacks often security and date/time compromised
attempts to get as unexpected occur by audit stamps for low drivers to prevent
"under" a disk accesses, creating system capabilities level system access
security system unexplained emergencies to into even the files or Monitor
by accessing device failures, cause system lowest level changes in suspected access
very low level halted security reloading or software, such sector/block points to attempt
system functions software, etc. initialization as device counts for trace back to
(e.g., device drivers, shared device drivers perpetrator
drivers, OS libraries, etc.
kernels)
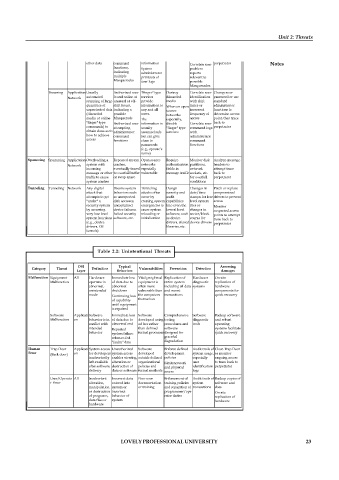
Table 2.2: Unintentional Threats
OSI Typical Assessing
Category Threat Definition Vulnerabilities Prevention Detection
Layer Behaviors damages
Malfunction Equipment All Hardware Immediate loss Vital peripheral Replication of Hardware On-site
Malfunction operates in of data due to equipment is entire system diagnostic replication of
abnormal, abnormal often more including all data systems hardware
unintended shutdown vulnerable than and recent components for
mode Continuing loss the computers transactions quick recovery
of capability themselves
until equipment
is repaired
Software Applicati Software Immediate loss Software Comprehensive Software Backup software
Malfunction on behavior is in of data due to developed using testing diagnostic and robust
conflict with abnormal end ad hoc rather procedures and tools operating
intended Repeated than defined software systems facilitate
behavior system failure formal processes designed for quick recovery
when re-fed graceful
"faulty" data degradation
Human Trap Door Applicati System access Unauthorized Software Enforce defined Audit trails of Close Trap Door
Error on for developers system access developed development system usage, or monitor
(Back door)
inadvertently enables viewing, outside defined policies especially ongoing access
left available alteration or organizational Limit network user to trace back to
after software destruction of policies and and physical identification perpetrator
delivery data or software formal methods access logs
User/Operato All Inadvertent Incorrect data Poor user Enforcement of Audit trails of Backup copies of
r Error alteration, entered into documentation training policies system software and
manipulation system or or training and separation of transactions data
or destruction incorrect programmer/ope On-site
of programs, behavior of rator duties replication of
data files or system hardware
hardware
LOVELY PROFESSIONAL UNIVERSITY 23