Page 65 - DCAP309_INFORMATION_SECURITY_AND_PRIVACY
P. 65
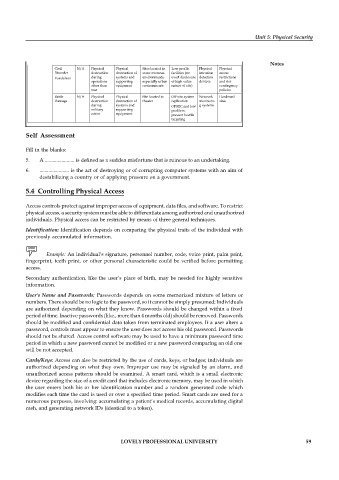
Typical
OSI
Countermea
Detection
Category
Threat
Vulnerabilities
Prevention
Definition
Behaviors
Layer
sures
N/A
Physical
Physical
Fire
Environment
Damage
near potential
replication,
FM200 fire
smoke
destruction of destruction of
extinguishers
fire hazards,
alarms
systems and
equipment
while costly,
e.g., fuel storage provides
due to fire or
supporting
mitigate
smoke
backup
electrical and
tanks
equipment
water
capability
damage
damage
N/A
Physical
Computer
Physical
Systems located
Water
Off-site system
Water
destruction of destruction of
below ground or replication
rooms
Damage
detection
systems and
equipment
near sprinkler
equipped
devices
with
due to water
supporting
systems
emergency
(including Physical Systems located Off-site system On-site Halon gas or
equipment
sprinkler) drainage
damage capabilities
Power Loss N/A Computers or Immediate loss Sites fed by Dual or Power Uninterrupti
vital of data due to above ground separate feeder level alert ble Power
supporting abnormal power lines are lines for monitors Supplies
equipment shutdow, even particularly computers and (UPS)
fail due to after power vulnerable supporting Full scale
lack of power returns Power loss to equipment standby Unit 5: Physical Security
Continuing computer room power
loss of air conditioners facilities
capability until can also be an where
power returns issue economically
feasible
Notes
Civil N/A Physical Physical Sites located in Low profile Physical Physical
Disorder destruction destruction of some overseas facilities (no intrusion access
Vandalism during systems and environments, overt disclosure detection restrictions
operations supporting especially urban of high value devices and riot
other than equipment environments nature of site) contingency
war policies
Battle N/A Physical Physical Site located in Off-site system Network Hardened
Damage destruction destruction of theater replication monitorin sites
during systems and OPSEC and low g systems
military supporting profile to
action equipment prevent hostile
targeting
Self Assessment
Fill in the blanks:
5. A ....................... is defined as a sudden misfortune that is ruinous to an undertaking.
6. ....................... is the act of destroying or of corrupting computer systems with an aim of
destabilizing a country or of applying pressure on a government.
5.4 Controlling Physical Access
Access controls protect against improper access of equipment, data files, and software. To restrict
physical access, a security system must be able to differentiate among authorized and unauthorized
individuals. Physical access can be restricted by means of three general techniques.
Identification: Identification depends on comparing the physical traits of the individual with
previously accumulated information.
Example: An individual‘s signature, personnel number, code, voice print, palm print,
fingerprint, teeth print, or other personal characteristic could be verified before permitting
access.
Secondary authentication, like the user‘s place of birth, may be needed for highly sensitive
information.
User‘s Name and Passwords: Passwords depends on some memorized mixture of letters or
numbers. There should be no logic to the password, so it cannot be simply presumed; Individuals
are authorized depending on what they know. Passwords should be changed within a fixed
period of time. Inactive passwords (like., more than 4 months old) should be removed. Passwords
should be modified and confidential data taken from terminated employees. If a user alters a
password, controls must appear to ensure the user does not access his old password. Passwords
should not be shared. Access control software may be used to have a minimum password time
period in which a new password cannot be modified or a new password comparing an old one
will be not accepted.
Cards/Keys: Access can also be restricted by the use of cards, keys, or badges; individuals are
authorized depending on what they own. Improper use may be signaled by an alarm, and
unauthorized access patterns should be examined. A smart card, which is a small electronic
device regarding the size of a credit card that includes electronic memory, may be used in which
the user enters both his or her identification number and a random generated code which
modifies each time the card is used or over a specified time period. Smart cards are used for a
numerous purposes, involving: accumulating a patient‘s medical records, accumulating digital
cash, and generating network IDs (identical to a token).
LOVELY PROFESSIONAL UNIVERSITY 59