Page 398 - DCAP103_Principle of operating system
P. 398
Unit 13: Input/Output and Security of Windows
the access control list assigned to objects created by the process if no other ACL is specified. The Notes
user SID tells who owns the process. The restricted SIDs are to allow untrustworthy processes
to take part in jobs with trustworthy processes but with less power to do damage.
Finally, the privileges listed, if any, give the process special powers, such as the right to
shut the machine down or access files to which access would otherwise be denied. In effect,
the privileges split up the power of the superuser into several rights that can be assigned to
processes individually. In this way, a user can be given some superuser power, but not all of
it. In summary, the access token tells who owns the process and which defaults and powers
are associated with it.
Figure 13.13: Structure of an Access Token
Header Expiration Groups Default User Group Restricted Privileges
time DACL SID SID SIDs
When a user logs in, winlogon gives the initial process an access token. Subsequent processes
normally inherit this token on down the line. A process’ access token initially applies to all the
threads in the process. However, a thread can acquire a different access token during execution,
in which case the thread’s access token overrides the process’ access token. In particular, a
client thread can pass its access token to a server thread to allow the server to access the client’s
protected files and other objects. This mechanism is called impersonation.
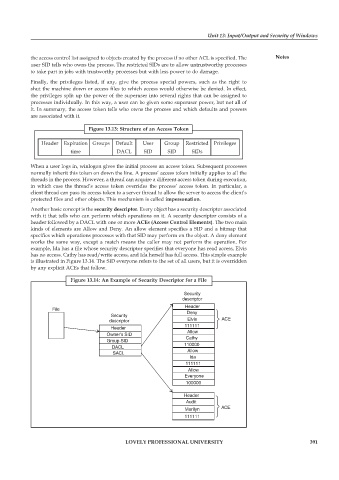
Another basic concept is the security descriptor. Every object has a security descriptor associated
with it that tells who can perform which operations on it. A security descriptor consists of a
header followed by a DACL with one or more ACEs (Access Control Elements). The two main
kinds of elements are Allow and Deny. An allow element specifies a SID and a bitmap that
specifies which operations processes with that SID may perform on the object. A deny element
works the same way, except a match means the caller may not perform the operation. For
example, Ida has a file whose security descriptor specifies that everyone has read access, Elvis
has no access. Cathy has read/write access, and Ida herself has full access. This simple example
is illustrated in Figure 13.14. The SID everyone refers to the set of all users, but it is overridden
by any explicit ACEs that follow.
Figure 13.14: An Example of Security Descriptor for a File
LOVELY PROFESSIONAL UNIVERSITY 391