Page 399 - DCAP103_Principle of operating system
P. 399
Principles of Operating Systems
Notes In addition to the DACL, a security descriptor also has a SACL (System Access Control List),
which is like a DACL except that it specifies not who may use the object, but which operations
on the object are recorded in the system-wide security event log. In Figure 13.14, every operation
that Marilyn performs on the file will be logged. Windows 2000 provides additional auditing
features to log sensitive accesses.
13.3.2 Security API Calls
Most of the Windows 2000 access control mechanism is based on security descriptors. The
usual pattern is that when a process creates an object, it provides a security descriptor as one
of the parameters to the CreateProcess, CreateFile, or other object creation call. This security
descriptor then becomes the security descriptor attached to the object, as we saw in Figure 13.14.
If no security descriptor is provided in the object creation call, the default security in the caller’s
access token (see Figure 13.13) is used instead.
Many of the Win32 API security calls relate to the management of security descriptors, so we
will focus on those here. The most important calls are listed in Figure 13.15. To create a security
descriptor, storage for it is first allocated and then initialized using InitializeSecurityDescriptor.
This call fills in the header. If the owner SID is not known, it can be looked up by name using
LookupAccountSid. It can then be inserted into the security descriptor. The same holds for the
group SID, if any. Normally, these will be the caller’s own SID and one of the caller’s groups,
but the system administrator can fill in any SIDs.
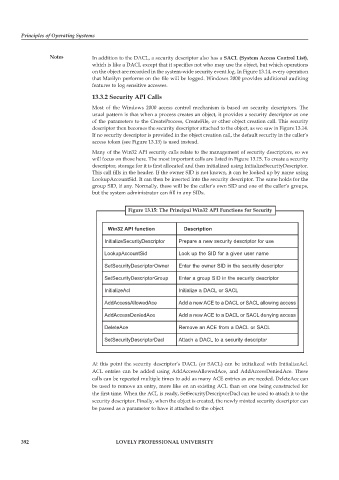
Figure 13.15: The Principal Win32 API Functions for Security
Win32 API function Description
InitializeSecurityDescriptor Prepare a new security descriptor for use
LookupAccountSid Look up the SID for a given user name
SetSecurityDescriptorOwner Enter the owner SID in the security descriptor
SetSecurityDescriptorGroup Enter a group SID in the security descriptor
InitializeAcl Initialize a DACL or SACL
AddAccessAllowedAce Add a new ACE to a DACL or SACL allowing access
AddAccessDeniedAce Add a new ACE to a DACL or SACL denying access
DeleteAce Remove an ACE from a DACL or SACL
SetSecurityDescriptorDacl Attach a DACL to a security descriptor
At this point the security descriptor’s DACL (or SACL) can be initialized with InitializeAcl.
ACL entries can be added using AddAccessAllowedAce, and AddAccessDeniedAce. These
calls can be repeated multiple times to add as many ACE entries as are needed. DeleteAce can
be used to remove an entry, more like on an existing ACL than on one being constructed for
the first time. When the ACL is ready, SetSecurityDescriptorDacl can be used to attach it to the
security descriptor. Finally, when the object is created, the newly minted security descriptor can
be passed as a parameter to have it attached to the object.
392 LOVELY PROFESSIONAL UNIVERSITY