Page 193 - DCAP403_Operating System
P. 193
Operating System
Notes Role-based Access Control
Role-based access control (RBAC) enforces access controls depending upon a user’s role(s).
Roles represent specific organisational duties and are commonly mapped to job titles such as
“Administrator,” “Developer,” or “System Analyst.” Obviously, these roles require vastly
different network access privileges.
Role defi nitions and associated access rights must be based upon a thorough understanding of
an organisation’s security policy. In fact, roles and the access rights that go with them should be
directly related to elements of the security policy.
Take-grant Model
The access matrix model, properly interpreted, corresponds very well to a wide variety of actual
computer system implementations. The simplicity of the model, its definition of subjects, objects,
and access control mechanisms, is very appealing. Consequently, it has served as the basis for
a number of other models and development efforts. You now discuss a model based on access
matrix.
Take-grant models use graphs to model access control. They have been well researched. Although
explained in the terms of graph theory, these models are fundamentally access matrix models.
The graph structure can be represented as an adjacency matrix, and labels on the arcs can be
coded as different values in the matrix.
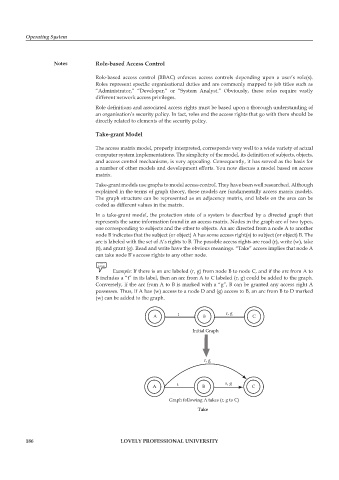
In a take-grant model, the protection state of a system is described by a directed graph that
represents the same information found in an access matrix. Nodes in the graph are of two types,
one corresponding to subjects and the other to objects. An arc directed from a node A to another
node B indicates that the subject (or object) A has some access right(s) to subject (or object) B. The
arc is labeled with the set of A’s rights to B. The possible access rights are read (r), write (w), take
(t), and grant (g). Read and write have the obvious meanings. “Take” access implies that node A
can take node B’s access rights to any other node.
Example: If there is an arc labeled (r, g) from node B to node C, and if the arc from A to
B includes a “t” in its label, then an arc from A to C labeled (r, g) could be added to the graph.
Conversely, if the arc from A to B is marked with a “g”, B can be granted any access right A
possesses. Thus, if A has (w) access to a node D and (g) access to B, an arc from B to D marked
(w) can be added to the graph.
A t B r, g C
Initial Graph
r, g
A t B r, g C
Graph following A takes (r, g to C)
Take
186 LOVELY PROFESSIONAL UNIVERSITY