Page 235 - DCAP403_Operating System
P. 235
Operating System
Notes 12.3 Symmetric or Secret-key Encryption
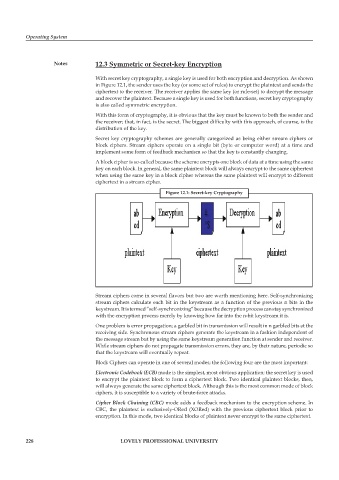
With secret key cryptography, a single key is used for both encryption and decryption. As shown
in Figure 12.1, the sender uses the key (or some set of rules) to encrypt the plaintext and sends the
ciphertext to the receiver. The receiver applies the same key (or rule-set) to decrypt the message
and recover the plaintext. Because a single key is used for both functions, secret key cryptography
is also called symmetric encryption.
With this form of cryptography, it is obvious that the key must be known to both the sender and
the receiver; that, in fact, is the secret. The biggest difficulty with this approach, of course, is the
distribution of the key.
Secret key cryptography schemes are generally categorized as being either stream ciphers or
block ciphers. Stream ciphers operate on a single bit (byte or computer word) at a time and
implement some form of feedback mechanism so that the key is constantly changing.
A block cipher is so-called because the scheme encrypts one block of data at a time using the same
key on each block. In general, the same plaintext block will always encrypt to the same ciphertext
when using the same key in a block cipher whereas the same plaintext will encrypt to different
ciphertext in a stream cipher.
Figure 12.1: Secret-key Cryptography
Stream ciphers come in several flavors but two are worth mentioning here. Self-synchronizing
stream ciphers calculate each bit in the keystream as a function of the previous n bits in the
keystream. It is termed “self-synchronizing” because the decryption process can stay synchronized
with the encryption process merely by knowing how far into the n-bit keystream it is.
One problem is error propagation; a garbled bit in transmission will result in n garbled bits at the
receiving side. Synchronous stream ciphers generate the keystream in a fashion independent of
the message stream but by using the same keystream generation function at sender and receiver.
While stream ciphers do not propagate transmission errors, they are, by their nature, periodic so
that the keystream will eventually repeat.
Block Ciphers can operate in one of several modes; the following four are the most important:
Electronic Codebook (ECB) mode is the simplest, most obvious application: the secret key is used
to encrypt the plaintext block to form a ciphertext block. Two identical plaintext blocks, then,
will always generate the same ciphertext block. Although this is the most common mode of block
ciphers, it is susceptible to a variety of brute-force attacks.
Cipher Block Chaining (CBC) mode adds a feedback mechanism to the encryption scheme. In
CBC, the plaintext is exclusively-ORed (XORed) with the previous ciphertext block prior to
encryption. In this mode, two identical blocks of plaintext never encrypt to the same ciphertext.
228 LOVELY PROFESSIONAL UNIVERSITY