Page 239 - DCAP403_Operating System
P. 239
Operating System
Notes The DES algorithm is well known. However, since the key is only 56 bit long, there is some
concern about security of data. A modification to DES is triple-DES and this improves the security
aspects considerably.
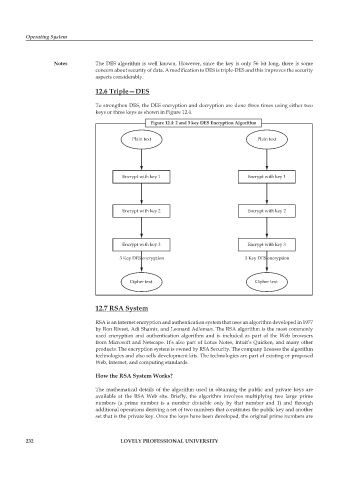
12.6 Triple—DES
To strengthen DES, the DES encryption and decryption are done three times using either two
keys or three keys as shown in Figure 12.4.
Figure 12.4: 2 and 3 key DES Encryption Algorithm
Plain text Plain text
Encrypt with key 1 Encrypt with key 1
Encrypt with key 2 Encrypt with key 2
Encrypt with key 3 Encrypt with key 3
3 Key DES encryption 3 Key DES encryption
Cipher text Cipher text
12.7 RSA System
RSA is an Internet encryption and authentication system that uses an algorithm developed in 1977
by Ron Rivest, Adi Shamir, and Leonard Adleman. The RSA algorithm is the most commonly
used encryption and authentication algorithm and is included as part of the Web browsers
from Microsoft and Netscape. It’s also part of Lotus Notes, Intuit’s Quicken, and many other
products. The encryption system is owned by RSA Security. The company licenses the algorithm
technologies and also sells development kits. The technologies are part of existing or proposed
Web, Internet, and computing standards.
How the RSA System Works?
The mathematical details of the algorithm used in obtaining the public and private keys are
available at the RSA Web site. Briefly, the algorithm involves multiplying two large prime
numbers (a prime number is a number divisible only by that number and 1) and through
additional operations deriving a set of two numbers that constitutes the public key and another
set that is the private key. Once the keys have been developed, the original prime numbers are
232 LOVELY PROFESSIONAL UNIVERSITY