Page 242 - DCAP403_Operating System
P. 242
Unit 12: Security Solution
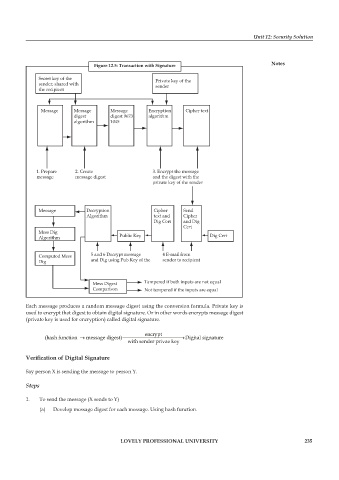
Figure 12.5: Transaction with Signature Notes
Secret key of the Private key of the
sender, shared with sender
the recipient
Message Message Message Encryption Cipher text
digest digest 9673 algorithm
algorithm 1045
1. Prepare 2. Create 3. Encrypt the message
message message digest and the digest with the
private key of the sender
Message Decryption Cipher Send
Algorithm text and Cipher
Dig Cert and Dig
Cert
Mess Dig
Algorithm Public Key Dig Cert
Computed Mess 5 and 6 Decrypt message 4 E-mail from
Dig and Dig using Pub Key of the sender to recipient
Mess Digest Tampered if both inputs are not equal
Comparison Not tempered if the inputs are equal
Each message produces a random message digest using the conversion formula. Private key is
used to encrypt that digest to obtain digital signature. Or in other words encrypts message digest
(private key is used for encryption) called digital signature.
encrypt
(hash function → message digest)⎯⎯⎯⎯⎯⎯⎯⎯⎯⎯⎯→ Digital signature
with sender privae key
Verification of Digital Signature
Say person X is sending the message to person Y.
Steps
1. To send the message (X sends to Y)
(a) Develop message digest for each message. Using hash function.
LOVELY PROFESSIONAL UNIVERSITY 235