Page 232 - DCAP311_DCAP607_WIRELESS_NETWORKS
P. 232
Wireless Networks
Notes virtual keyboard, and so on. KBA is used also as an identity-verification method for self-
service password-reset processes; but, when implemented effectively, they can be used
as methods to complement primary authentication. This approach moderately improves
authentication strength, as it is still single-factor (in-band within the browser) and prone to
phishing attacks, but it might be sufficient for some Web sites.
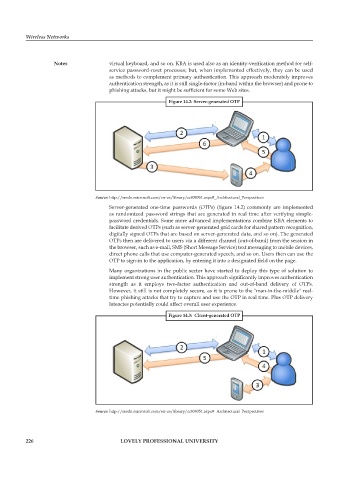
Figure 14.2: Server-generated OTP
Source: http://msdn.microsoft.com/en-us/library/cc838351.aspx#_Architectural_Perspectives
Server-generated one-time passwords (OTPs) (figure 14.2) commonly are implemented
as randomized password strings that are generated in real time after verifying simple-
password credentials. Some more advanced implementations combine KBA elements to
facilitate derived OTPs (such as server-generated grid cards for shared pattern recognition,
digitally signed OTPs that are based on server-generated data, and so on). The generated
OTPs then are delivered to users via a different channel (out-of-band) from the session in
the browser, such as e-mail, SMS (Short Message Service) text messaging to mobile devices,
direct phone calls that use computer-generated speech, and so on. Users then can use the
OTP to sign-in to the application, by entering it into a designated field on the page.
Many organizations in the public sector have started to deploy this type of solution to
implement strong user authentication. This approach significantly improves authentication
strength as it employs two-factor authentication and out-of-band delivery of OTPs.
However, it still is not completely secure, as it is prone to the "man-in-the-middle" real-
time phishing attacks that try to capture and use the OTP in real time. Plus OTP delivery
latencies potentially could affect overall user experience.
Figure 14.3: Client-generated OTP
Source: http://msdn.microsoft.com/en-us/library/cc838351.aspx#_Architectural_Perspectives
226 LOVELY PROFESSIONAL UNIVERSITY