Page 233 - DCAP311_DCAP607_WIRELESS_NETWORKS
P. 233
Unit 14: Authentication
Client-generated one-time passwords (figure 14.3) are similar to conventional OTP Notes
hardware tokens (such as RSA SecurID, VeriSign VIP OTP, and so on). However, with
the level of near-ubiquitous proliferation of mobile devices today, cellular phones have
become a viable alternative as the soft-token (or "something held") authentication factor.
In this case, individualized cryptographic software components can be installed on mobile
devices to generate time-based or event-based OTPs. Users then can use the OTP to sign-
in to the application after authenticating simple Web-based credentials (examples include
RSA SecurID software, Java ME applications, and so on). This approach has the benefits
of OTPs, not having to deal with out-of-band delivery latencies and inconsistent service
coverage.
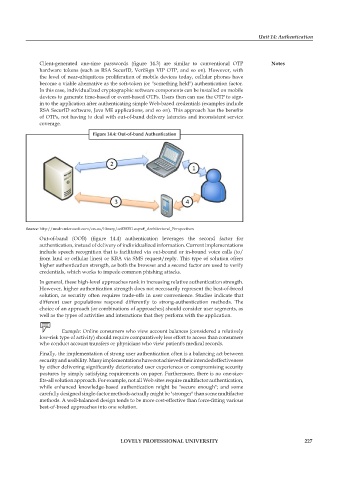
Figure 14.4: Out-of-band Authentication
Source: http://msdn.microsoft.com/en-us/library/cc838351.aspx#_Architectural_Perspectives
Out-of-band (OOB) (figure 14.4) authentication leverages the second factor for
authentication, instead of delivery of individualized information. Current implementations
include speech recognition that is facilitated via out-bound or in-bound voice calls (to/
from land or cellular lines) or KBA via SMS request/reply. This type of solution offers
higher authentication strength, as both the browser and a second factor are used to verify
credentials, which works to impede common phishing attacks.
In general, these high-level approaches rank in increasing relative authentication strength.
However, higher authentication strength does not necessarily represent the best-of-breed
solution, as security often requires trade-offs in user convenience. Studies indicate that
different user populations respond differently to strong-authentication methods. The
choice of an approach (or combinations of approaches) should consider user segments, as
well as the types of activities and interactions that they perform with the application.
Example: Online consumers who view account balances (considered a relatively
low-risk type of activity) should require comparatively less effort to access than consumers
who conduct account transfers or physicians who view patient's medical records.
Finally, the implementation of strong user authentication often is a balancing act between
security and usability. Many implementations have not achieved their intended effectiveness
by either delivering significantly deteriorated user experiences or compromising security
postures by simply satisfying requirements on paper. Furthermore, there is no one-size-
fits-all solution approach. For example, not all Web sites require multifactor authentication,
while enhanced knowledge-based authentication might be "secure enough"; and some
carefully designed single-factor methods actually might be "stronger" than some multifactor
methods. A well-balanced design tends to be more cost-effective than force-fitting various
best-of-breed approaches into one solution.
LOVELY PROFESSIONAL UNIVERSITY 227