Page 228 - DCAP403_Operating System
P. 228
Unit 11: System Security
have taken advantage of this to create their own macros that, depending on the application, Notes
can destroy your data or crash your computer.
8. Viruses: Probably the most well-known threat is computer viruses. A virus is a small
program that can copy itself to other computers. This way it can spread quickly from one
system to the next. Viruses range from harmless messages to erasing all of your data.
9. Spam: Typically harmless but always annoying, spam is the electronic equivalent of junk
mail. Spam can be dangerous though. Quite often it contains links to Web sites. Be careful
of clicking on these because you may accidentally accept a cookie that provides a backdoor
to your computer.
10. Redirect bombs: Hackers can use ICMP to change (redirect) the path information takes by
sending it to a different router. This is one of the ways that a denial of service attack is set
up.
11. Source routing: In most cases, the path a packet travels over the Internet (or any other
network) is determined by the routers along that path. But the source providing the packet
can arbitrarily specify the route that the packet should travel. Hackers sometimes take
advantage of this to make information appear to come from a trusted source or even from
inside the network! Most firewall products disable source routing by default.
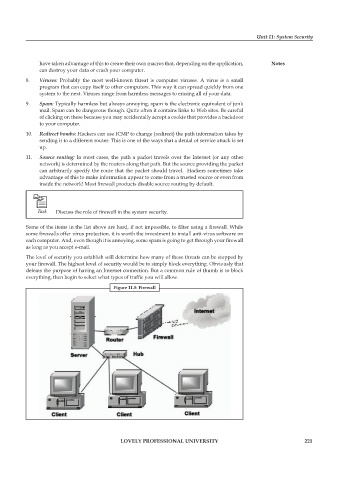
Task Discuss the role of firewall in the system security.
Some of the items in the list above are hard, if not impossible, to filter using a fi rewall. While
some firewalls offer virus protection, it is worth the investment to install anti-virus software on
each computer. And, even though it is annoying, some spam is going to get through your fi rewall
as long as you accept e-mail.
The level of security you establish will determine how many of these threats can be stopped by
your firewall. The highest level of security would be to simply block everything. Obviously that
defeats the purpose of having an Internet connection. But a common rule of thumb is to block
everything, then begin to select what types of traffic you will allow.
Figure 11.5: Firewall
LOVELY PROFESSIONAL UNIVERSITY 221