Page 266 - DCAP403_Operating System
P. 266
Unit 13: Case Study: Linux
This illustrates an interesting point about sharing pages: the shared physical page does not have Notes
to exist at the same place in virtual memory for any or all of the processes sharing it.
13.5.4 Physical and Virtual Addressing Modes
It does not make much sense for the operating system itself to run in virtual memory. This would
be a nightmare situation where the operating system must maintain page tables for itself. Most
multi-purpose processors support the notion of a physical address mode as well as a virtual
address mode. Physical addressing mode requires no page tables and the processor does not
attempt to perform any address translations in this mode. The Linux kernel is linked to run in
physical address space.
The Alpha AXP processor does not have a special physical addressing mode. Instead, it divides
up the memory space into several areas and designates two of them as physically mapped
addresses. This kernel address space is known as KSEG address space and it encompasses all
addresses upwards from 0xfffffc0000000000. In order to execute from code linked in KSEG (by
definition, kernel code) or access data there, the code must be executing in kernel mode. The
Linux kernel on Alpha is linked to execute from address 0xfffffc0000310000.
13.5.5 Access Control
The page table entries also contain access control information. As the processor is already using
the page table entry to map a processes virtual address to a physical one, it can easily use the
access control information to check that the process is not accessing memory in a way that it
should not.
There are many reasons why you would want to restrict access to areas of memory. Some memory,
such as that containing executable code, is naturally read only memory; the operating system
should not allow a process to write data over its executable code. By contrast, pages containing
data can be written to but attempts to execute that memory as instructions should fail. Most
processors have at least two modes of execution: kernel and user. You would not want kernel
code executing by a user or kernel data structures to be accessible except when the processor is
running in kernel mode.
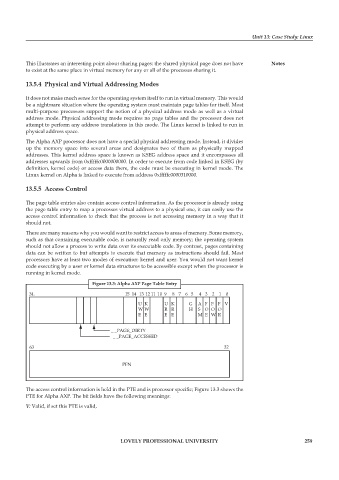
Figure 13.3: Alpha AXP Page Table Entry
3L 15 14 13 12 11 10 9 8 76 5 4 3210
U K U K G A F F F V
W W R R H S O O O
E E E E M E W R
_ _PAGE_DIRTY
_ _PAGE_ACCESSED
63 32
PFN
The access control information is held in the PTE and is processor specific; Figure 13.3 shows the
PTE for Alpha AXP. The bit fields have the following meanings:
V: Valid, if set this PTE is valid,
LOVELY PROFESSIONAL UNIVERSITY 259