Page 124 - DCAP309_INFORMATION_SECURITY_AND_PRIVACY
P. 124
Information Security and Privacy
Notes An analogy for public-key encryption is that of a locked mailbox with a mail slot. The mail slot is
exposed and accessible to the public; its location (the street address) is in essence the public key.
Anyone knowing the street address can go to the door and drop a written message through the
slot; however, only the person who possesses the key can open the mailbox and read the message.
An analogy for digital signatures is the sealing of an envelope with a personal wax seal. The
message can be opened by anyone, but the presence of the seal authenticates the sender.
A central problem for public-key cryptography is proving that a public key is authentic, and has
not been tampered with or replaced by a malicious third party. The usual approach to this
problem is to use a Public-key Infrastructure (PKI), in which one or more third parties, known
as certificate authorities, certify ownership of key pairs. Another approach, used by PGP, is the
“web of trust” method to ensure authenticity of key pairs.
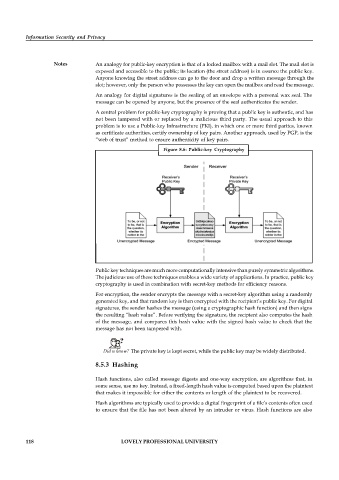
Figure 8.6: Public-key Cryptography
Public key techniques are much more computationally intensive than purely symmetric algorithms.
The judicious use of these techniques enables a wide variety of applications. In practice, public key
cryptography is used in combination with secret-key methods for efficiency reasons.
For encryption, the sender encrypts the message with a secret-key algorithm using a randomly
generated key, and that random key is then encrypted with the recipient’s public key. For digital
signatures, the sender hashes the message (using a cryptographic hash function) and then signs
the resulting “hash value”. Before verifying the signature, the recipient also computes the hash
of the message, and compares this hash value with the signed hash value to check that the
message has not been tampered with.
Did u know? The private key is kept secret, while the public key may be widely distributed.
8.5.3 Hashing
Hash functions, also called message digests and one-way encryption, are algorithms that, in
some sense, use no key. Instead, a fixed-length hash value is computed based upon the plaintext
that makes it impossible for either the contents or length of the plaintext to be recovered.
Hash algorithms are typically used to provide a digital fingerprint of a file’s contents often used
to ensure that the file has not been altered by an intruder or virus. Hash functions are also
118 LOVELY PROFESSIONAL UNIVERSITY